-
Apple on Wednesday revised its documentation pertaining to its mercenary spyware threat notification system to mention that it alerts users when they may have been individually targeted by such attacks. It also specifically called out companies like NSO Group for developing commercial surveillance tools such as Pegasus that are used by state actors to pull off “individually targeted
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Fortinet has released patches to address a critical security flaw impacting FortiClientLinux that could be exploited to achieve arbitrary code execution. Tracked as CVE-2023-45590, the vulnerability carries a CVSS score of 9.4 out of a maximum of 10. “An Improper Control of Generation of Code (‘Code Injection’) vulnerability [CWE-94] in FortiClientLinux may allow an unauthenticated attacker to
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cybersecurity experts have uncovered a failed attempt by the notorious Russia-based Turla Advanced Persistent Threat (APT) group to infiltrate an Albanian organization.
This incident is part of a broader cyber espionage campaign targeting European countries, with Poland also falling victim to these sophisticated attacks.
The discovery aligns with the ongoing geopolitical tensions and highlights state-aligned actors’ escalating cyber warfare tactics.
Are you from the SOC and DFIR Teams? – Analyse linux Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.The Failed Infiltration
On March 26, a user located in Albania uploaded a file to the VirusTotal web interface, which revealed the attempted breach in Albania.
The file, named “Firewall_Bllok_IP.txt.txt,” contained a list of IP addresses, including the address 91[.]193[.]18[.]120.
Cisco Talos has flagged this particular IP as a command and control server associated with the “TinyTurla-NG” (TTNG) backdoor, marking it as a key indicator of compromise.
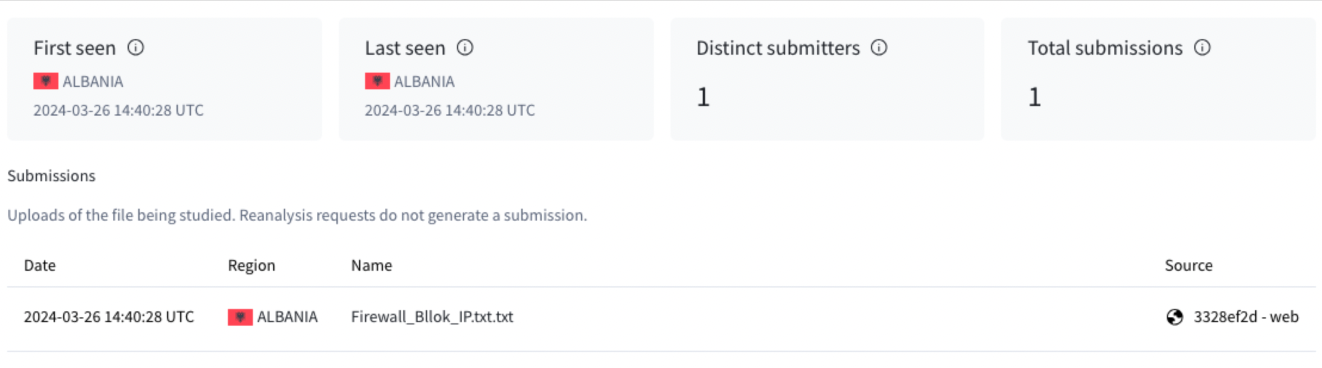
Unique file uploaded manually from Albania-based IP address on March 26 to the VirusTotal user web interface
with ”bllok”(block) written in Albanian.Analysis of the file confirmed its authenticity. Multiple antivirus vendors recognized all listed IP addresses as malicious.
The plaintext file only lists IP addresses Turla APT’s Expanding Campaign
The Turla APT group, known for its sophisticated cyber espionage operations, has historically targeted organizations with links to government sectors across Baltic and Eastern European countries.
The recent activities in Albania and Poland underscore the group’s ongoing efforts to gather intelligence and exert influence amidst the broader context of the war in Ukraine.
These incidents provide crucial insights into the possible scope of Russia-based APT operations, which continue to pose a significant threat to European security.
Implications for European Security
The targeting of Albania by the Turla APT group is a stark reminder of the persistent cyber threats facing European organizations.
These entities often possess valuable information and maintain critical infrastructure, so they are high-value targets for espionage activities.
The incident underscores the need for heightened cybersecurity measures and international cooperation to counteract the sophisticated tactics employed by state-aligned APT groups.
Looking Ahead
The cybersecurity community remains vigilant as the Turla APT group continues to refine its tactics and target European organizations.
The failed attempt in Albania is a critical reminder of the ongoing cyber warfare landscape, where information is a valuable commodity, and security is perpetually at risk.
With the geopolitical tensions showing no signs of abating, European organizations must remain on high alert and prioritize cybersecurity to thwart future espionage attempts by state-aligned actors.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post Cyber Espionage: Turla APT Hackers Attack European Organization With Backdoor appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
US is “taking steps” and “working through” the problem with SpaceX and Ukraine, space-policy leader says.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In House hearing, Gen. Cavoli laid out the consequences of more House inaction on aid.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A comprehensive four-year study of brute-force attacks against SSH servers has revealed an alarming increase in the frequency and sophistication of these cyber attacks on internet-connected systems.
The research by scientists at the University of Utah provides unprecedented insight into the evolving tactics used by attackers attempting to gain unauthorized access to servers, routers, IoT devices and more.
“SSH brute-force attacks are not only persistent, but are rapidly growing more aggressive,” said Sachin Kumar Singh, a PhD student who led the study. “Our data shows the daily number of attack attempts is skyrocketing, especially in recent years.”
The researchers analyzed over 427 million failed SSH login attempts across more than 500 servers on CloudLab, a public cloud platform used by academic researchers worldwide. Their findings paint a sobering picture of the modern cybersecurity landscape.
Shifting Targets
While attackers have historically focused on guessing common administrator usernames like “root” and “admin”, the study found a notable shift in recent years.
Cyber criminals now heavily target usernames associated with cloud service images, network devices, IoT products and specific software packages
“Attackers are going after usernames for everything from internet routers and database servers to gaming software and Linux distributions intended for cloud use,” explained Singh.
“They are trying to compromise a wide range of devices and services connected to the internet.”
The researchers identified spikes in attacks on certain usernames and devices immediately following public disclosures of related vulnerabilities, suggesting attackers rapidly operationalize new exploits.
Are you from the SOC and DFIR Teams? – Analyse linux Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.Persistent and Evolving Threats
Beyond changes in targeted usernames, the data revealed a wide diversity of attacker behaviors and persistence levels.
While over half of the attacks came from IP addresses that disappeared within 24 hours, some attackers persisted in their efforts for months or even years.
Certain attackers attempted just a handful of usernames, while others cycled through thousands of different combinations. The study also uncovered groups of attackers sharing identical lists of usernames across multiple IP addresses, indicating coordination.
“The brute-force attack landscape is highly dynamic,” said Robert Ricci, a research professor at the University of Utah who oversaw the study. “Attackers constantly adapt their tactics based on new intelligence and vulnerabilities. Defending against these threats requires advanced, evolving defensive measures.”
A Novel Defense
The researchers developed a defensive technique called Dictionary-Based Blocking (DBB) to counter the onslaught. By analyzing the username dictionaries used by attackers, DBB can block 99.5% of brute-force attacks while allowing legitimate user access.
When evaluated against the industry-standard Fail2ban tool, DBB achieved significantly higher blocking rates while reducing false positives by 83%. The researchers have deployed DBB on CloudLab, which prevents four out of five previously unblocked attacks.
“Dictionary-Based Blocking represents a new frontier in defending against brute-force attacks,” said Singh. “It could be a game changer for protecting critical infrastructure and internet services from these persistent threats.”
The research highlights the importance of secure practices like using key-based authentication and strong passwords. As attackers grow increasingly tenacious and innovative, novel defensive approaches will be essential to maintaining a safe internet ecosystem.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post Alert! Brute-Force SSH Attacks Rampant in the Wild: New Study From 427 Million Failed SSH Login Attempts appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The ODNI will soon release “extra safeguards” for protecting citizens’ privacy when buying datasets, a top Pentagon lawyer says.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
New strategy offers guidance on what the USSF wants to buy, but not how much it plans to spend.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Beijing has reached out on space safety, says U.S. Space Command leader, who also issued warnings about new PLA capabilities.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Law enforcement authorities successfully penetrated EncroChat, an encrypted chat program that is frequently used by criminals, in a ground-breaking operation that has shocked the world of organized crime.
This operation led to the arrest of hundreds of individuals involved in illegal activities across Europe and the seizure of substantial amounts of drugs, weapons, and cash.
The breach of EncroChat, once considered impenetrable, marks a significant victory in the ongoing battle against organized crime and raises important questions about privacy, security, and the limits of encryption technology.
This article discusses the successful efforts of the authorities to penetrate and gain control over the entire EncroChat instant messenger, which is commonly utilized by cybercriminals for communication.
The EncroChat Network
EncroChat offered encrypted phones at a high price, promising anonymity and security through end-to-end encrypted messaging (E2EE), with features designed to remove identifying information.
These devices, which cost around £900 each, with a subscription fee of £1,350 for six months, were tailored for privacy, with GPS, microphone, camera, and USB port all physically disconnected.
EncroChat’s services included encrypted messaging, ZRTP-based VOIP calls, and encrypted note-taking, operating on a dual-boot system with both EncroChat and Android OS.
The Breach
The operation to penetrate EncroChat began in December 2018 when a French court-authorized law enforcement to copy EncroChat’s virtual machines from a server in Roubaix, France. This led to legal maneuvers allowing authorities to install “computer data capture devices” on the server and intercept communications.
According to the presentation submitted at The Crypto Conference 2024, By March 2020, law enforcement had injected malware into EncroChat’s update servers, enabling them to collect both historical and live data from the devices.
This malware transmitted all stored data on the devices to the authorities and forwarded chat messages to French police servers in real-time without altering the encryption, thus maintaining the appearance of secure communication.
The breach resulted in more than 6,500 arrests and the seizure of over 900 million euros in assets. EncroChat, realizing the extent of the compromise, issued a warning and shut down its service in June 2020.
The operation revealed the scale of EncroChat’s use among criminals for coordinating illegal activities, including drug trafficking, violent attacks, and large-scale transports of illegal goods.
Are you from the SOC and DFIR Teams? – Analyse linux Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.Legal and Ethical Implications
The EncroChat breach has sparked a debate on the ethical and legal implications of law enforcement’s use of hacking and malware to combat crime.
While the operation has been hailed as a significant success in disrupting organized crime, it also raises concerns about privacy, the security of communication technologies, and the potential for abuse of such surveillance capabilities.

The operation’s reliance on malware and the covert interception of communications without users’ knowledge challenge traditional notions of privacy and legal process.
The successful breach of EncroChat represents a turning point in law enforcement’s approach to tackling encrypted networks used by criminals.
It underscores the vulnerabilities inherent in even the most secure communication systems and highlights the ongoing tension between privacy rights and the needs of law enforcement.
As technology continues to evolve, the balance between these competing interests will remain a contentious and critical issue for society.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post Real-World Law Enforcement Hack of Hackers End-to-Encrypted Chat Messenger appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


