-
Several security vulnerabilities disclosed in Brocade SANnav storage area network (SAN) management application could be exploited to compromise susceptible appliances. The 18 flaws impact all versions up to and including 2.3.0, according to independent security researcher Pierre Barre, who discovered and reported them. The issues range from incorrect firewall rules,
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Some router models have identified a security vulnerability that allows attackers to bypass authentication.
To exploit this vulnerability, an attacker must know the WiFi password or have an Ethernet connection to a device on the victim’s network.
Firmware updates that address this vulnerability are available for the following routers: RAX35 (version 1.0.6.106), RAX38 (version 1.0.6.106), and RAX40 (version 1.0.6.106).
It is strongly recommended that users download and install the latest firmware update as soon as possible.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe document details an authentication bypass vulnerability in a NETGEAR product and emphasizes the crucial importance of completing all the recommended steps to patch the vulnerability.
Failing to do so might expose your system, and NETGEAR is not responsible for any avoidable consequences.
This is only informational and does not carry any guarantees, as NETGEAR reserves the right to update the information as needed.
A critical vulnerability has been identified with a CVSS score of 8.4, which indicates a high-severity issue that can be exploited remotely (Attack Vector: Low) without complex actions by an attacker (Attack Complexity: Low).
No special privileges are required (Privileges Required: None), and no user interaction is needed (User Interaction: None).
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The vulnerability allows an attacker to compromise the affected system’s confidentiality, integrity, and availability (Scope: Unchanged; Confidentiality: High; Integrity: High; Availability: High).
NETGEAR recommends updating devices with the most recent firmware to implement security patches, bug fixes, and new features.
For NETGEAR app-supported devices, update the firmware through the corresponding app: the Orbi app for Orbi products, the Nighthawk app for NETGEAR WiFi routers, and the Insight app for some NETGEAR Business products (requires an Insight subscription).
For manual update instructions for unsupported devices, refer to the user manual, firmware release notes, or product support page.
The document underwent two revisions recently, as on April 15th, an advisory containing security recommendations was published.
Subsequently, on April 21st, the document was updated to acknowledge contributions from relevant parties, likely addressing collaborators, reviewers, or external sources that were not previously credited.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post NETGEAR buffer Overflow Vulnerability Let Attackers Bypass Authentication appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Hackers often target CrushFTP servers as they contain sensitive data and are used for file sharing and storage.
This makes them attractive targets for data theft and ransomware attacks for the threat actors.
Besides this, the vulnerabilities in CrushFTP servers can be exploited to gain unauthorized access to networks or distribute malware to connected systems.
Silent Push researchers recently identified that on April 19th, CrushFTP disclosed a critical zero-day vulnerability tracked as CVE-2024-4040 with a CVSS score of 9.8 in versions before 10.7.1/11.1.0.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideTechnical Analysis
The unauthenticated exploit allows escaping the Virtual File System via the WebInterface, gaining admin access and remote code execution capabilities.
CrushFTP urged immediate upgrades, even for DMZ deployments.
Researchers monitored the vulnerability, populating data feeds with vulnerable domains, IPs hosting the service, and infrastructure actively exploiting CVE-2024-4040 for early detection.
Silent Push conducts daily internet-wide scans that help categorize the data using SPQL to locate the associated infrastructure and content.
Leveraging the CVE-2024-4040 information, queries identified exploitable internet-exposed CrushFTP web interfaces.
The resulting vulnerable domains and IPs were clustered into two Bulk Data Feeds for enterprise customers to analyze the affected infrastructure.
Here below, we have mentioned those two Bulk Data Feeds:-
- CrushFTP Vulnerable Domains
- CrushFTP Vulnerable IPs
.webp)
Silent Push CrushFTP Bulk Data Feeds (Source – Silent Push) SPQL, at its core, is a tool of analysis for DNS data that spans over 90 categories. The map shows where CrushFTP interfaces are vulnerable to CVE-2024-4040 on a global scale.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
While most are in the US and Canada, many can be found across Europe as well as throughout:-
- South America
- Russia
- Asia
- Australia
.webp)
Global distribution of CrushFTP web interfaces (Source – Silent Push) This helps potential targets understand how big this issue really is, and it gives security professionals an idea of what they are up against.
Enterprise users can download raw data, as well as export bulk data feeds in the form of API endpoints that list CrushFTP domains and IPs that are susceptible to attacks.
With this information, security teams can identify weaknesses within their networks and inform risk-scoring systems used to evaluate outside dangers.
Meanwhile, a feed for early detection can track intrusion attempts in real time while simultaneously logging infrastructure related to those attempts so that it can be automatically blocked.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post 5000+ CrushFTP Servers Hacked Using Zero-Day Exploit appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
DDoS attacks are a significant and growing risk that can overpower websites, crash servers, and block out authorized users with never-ending waves of offensive traffic.
More than 13 million DDoS attacks were recorded in 2023 alone, which reveals the real danger of unmitigated attacks.
NetScout researchers recently discovered that threat actors executed 13,142,840 DDoS attacks targeted at organizations around the globe.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideTechnical Analysis
The outcomes are not limited to inconveniences alone. They bring all activities to a standstill, which involves critical services and consequently risks lives.
Also, businesses undergo financial losses coupled with losing customers’ trust as network operators face continuous storms that lead to security exhaustion.
If these establishments do not have adequate safeguards in place, their only choice is to respond aimlessly when it’s already too late.
Such moves may cause even greater harm while achieving no tangible results.
However, researchers urged that instead of reacting to hostile attacks at the eleventh hour, it is much better to be armed with the right information and protection tools in advance.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
For this reason, predictive and real-time threat intelligence that comes with advanced DDoS protection should be used to identify threats before they affect infrastructure.
Moreover, this allows immediate automated attack mitigation to reduce downtime by ensuring the continuity of operation for enterprises and the uninterrupted availability of vital services.
Converting reactive security into a proactive one enables businesses or organizations to plan strategically and ensures their security online against any threat to keep their systems protected.
Being aware of the changing threat environment is essential for predictive DDoS defense.
Recommendations
Here below, we have mentioned all the recommendations that will help in defending the DDoS attacks:-
- Implement DDoS mitigation solutions
- Regularly update and patch systems
- Make sure to implement web application firewalls (WAFs)
- Conduct regular security assessments
- Develop and test incident response plans
- Implement rate-limiting and traffic filtering
- Use content delivery networks (CDNs)
- Educate employees on security best practices
- Collaborate with security professionals and law enforcement
- Consistently implement redundancy and load balancing.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post 13,142,840 DDoS Attacks Targeted Organization Around The Globe appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In today’s digital world, where connectivity is rules all, endpoints serve as the gateway to a business’s digital kingdom. And because of this, endpoints are one of hackers’ favorite targets. According to the IDC, 70% of successful breaches start at the endpoint. Unprotected endpoints provide vulnerable entry points to launch devastating cyberattacks. With IT
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Fake browser updates are being used to push a previously undocumented Android malware called Brokewell. “Brokewell is a typical modern banking malware equipped with both data-stealing and remote-control capabilities built into the malware,” Dutch security firm ThreatFabric said in an analysis published Thursday. The malware is said to be in active development,
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Palo Alto Networks has shared remediation guidance for a recently disclosed critical security flaw impacting PAN-OS that has come under active exploitation. The vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), could be weaponized to obtain unauthenticated remote shell command execution on susceptible devices. It has been addressed in
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Hackers have leveraged an old Microsoft Office vulnerability, CVE-2017-8570, to deploy the notorious Cobalt Strike Beacon, targeting systems in Ukraine.
It has been closely monitoring the situation and has successfully detected all stages of the attack.
CVE-2017-8570: The Initial Vector
The attack begins with the exploitation of CVE-2017-8570, a vulnerability first identified in 2017.
This vulnerability allows attackers to execute arbitrary code via specially crafted files, making it a potent tool for initial access.
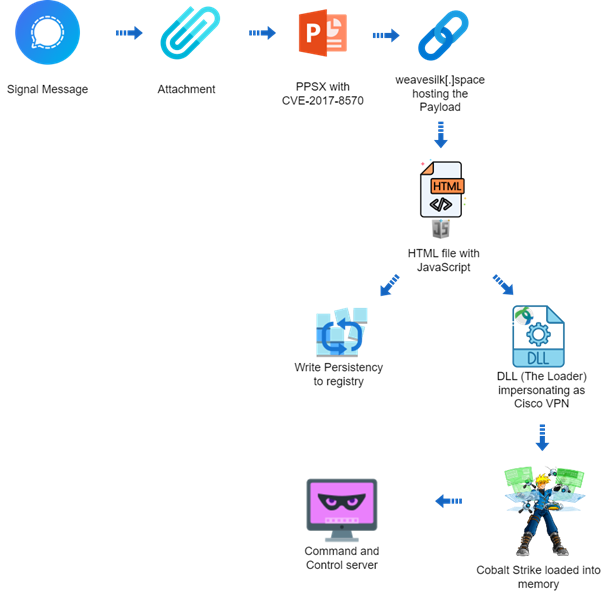
Campaign overview Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe attackers used a malicious PPSX (PowerPoint Slideshow) file, masquerading as an old US Army instruction manual for mine-clearing tank blades.

PPSX content The file was cleverly designed to bypass traditional security measures.
It included a remote relationship to an external OLE object, utilizing a “script:” prefix before an HTTPS URL to conceal the payload, avoid on-disk storage, and complicate analysis.
This technique highlights the attackers’ sophistication and focus on stealth and persistence.
Deep Instinct Threat Lab has played a crucial role in uncovering and analyzing this cyberattack.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Despite the detailed analysis, the operation could not be attributed to any known threat actor.
This lack of attribution adds complexity to the defense against these attacks, as understanding the adversary is critical to predicting and mitigating their tactics and techniques.
Cobalt Strike Beacon: Custom Loader
Central to this campaign is using a custom loader for the Cobalt Strike Beacon, a popular tool among cyber attackers due to its powerful command-and-control (C&C) capabilities and flexibility in deploying further payloads.
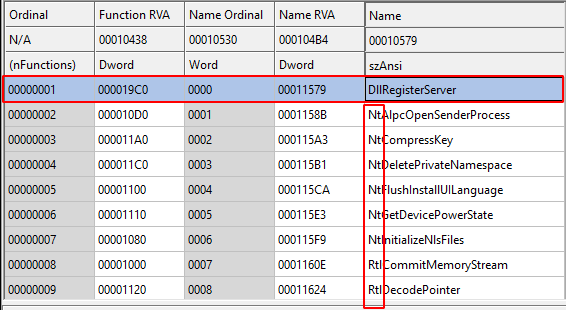
Loader export table The Cobalt Strike Beacon used in this attack was configured to communicate with a C&C server, cleverly disguised as a popular photography website but hosted under suspicious conditions.
The Beacon’s configuration included a cracked version of the software, indicated by a license_id of 0, and detailed instructions for C&C communications, including the domain name, URI, and public key for encrypted exchanges.
This setup not only facilitates robust control over the compromised systems but also complicates defenders’ efforts to intercept or disrupt communication.
Their technology has successfully detected all stages of the attack, from the initial document delivery to the execution of the Cobalt Strike Beacon.
This comprehensive detection capability is critical in a landscape where attackers constantly evolve their methods to evade detection.
Implications and Recommendations
This attack underscores the importance of vigilance and advanced detection capabilities in the cybersecurity domain.
Organizations are advised to update their systems regularly to patch known vulnerabilities like CVE-2017-8570.
Employ advanced threat detection solutions to identify and mitigate sophisticated threats, such as those posed by custom Cobalt Strike loaders.
As the situation develops, it remains crucial for cybersecurity communities to share information and collaborate on defense strategies, ensuring that they stay one step ahead of cyber adversaries.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Hackers Exploit Old Microsoft Office 0-day to Deliver Cobalt Strike appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In a historic move, Microsoft has made the source code for MS-DOS 4.0, one of the most influential operating systems of all time, publicly available on GitHub.
This decision marks a significant milestone in the company’s commitment to open-source software and preserving computing history.
“Today, we are thrilled to release the source code for MS-DOS 4.0 under the MIT license, fostering a spirit of open innovation,” said a Microsoft spokesperson. “This operating system’s 8086 assembly code, written over 45 years ago, is a remarkable testament to the ingenuity and dedication of our predecessors.”
The Legacy of MS-DOS
MS-DOS, short for Microsoft Disk Operating System, was the dominant operating system for personal computers throughout the 1980s and early 1990s.
Developed by Microsoft and first released in 1981, MS-DOS provided a command-line interface that allowed users to interact with their computers and run applications.

Despite its simplicity, MS-DOS played a crucial role in the personal computer revolution, enabling the widespread adoption of home and office computing.
It served as the foundation for many popular software applications and games, shaping the early days of the software industry.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The release of the MS-DOS 4.0 source code is significant for several reasons:
- Historical Preservation: By making the source code publicly available, Microsoft is ensuring that an important piece of computing history is preserved for future generations to study and learn from.
- Educational Value: Aspiring programmers and computer science students can now study the inner workings of a classic operating system, gaining valuable insights into low-level programming, memory management, and system architecture.
- Community Engagement: The open-source community can now contribute to the MS-DOS 4.0 codebase, potentially improving it, adding new features, or porting it to new platforms.
By releasing the MS-DOS 4.0 source code, Microsoft is embracing open-source principles and ensuring that this important piece of computing history is preserved for future generations.
The source code, now available on GitHub, provides a valuable resource for researchers, historians, and enthusiasts alike, allowing them to study and understand the inner workings of this iconic operating system.
Microsoft’s decision to open source MS-DOS 4.0 aligns with the company’s broader efforts to promote transparency and collaboration within the tech community. By making the source code publicly accessible, Microsoft encourages developers, researchers, and hobbyists to explore, learn from, and potentially build upon this historic codebase.
The release of the MS-DOS 4.0 source code on GitHub, a popular platform for open-source software development, presents exciting opportunities for collaboration and community engagement.
Developers and enthusiasts worldwide can now contribute to the project, propose improvements, fix bugs, or even create new applications based on the original codebase.
This move by Microsoft celebrates the company’s rich technological heritage and demonstrates its commitment to fostering open-source communities and encouraging innovation through shared knowledge and collaboration.
The release of the MS-DOS 4.0 source code is a significant milestone in preserving computing history and a testament to Microsoft’s embrace of open-source principles.
By making this iconic operating system’s source code publicly available, Microsoft is ensuring that MS-DOS’s legacy lives on, inspiring future generations of developers and researchers while promoting transparency and collaboration within the tech community.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Microsoft Publicly Releases MS-DOS 4.0 Source Code appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


