-
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. “The model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with the security mechanisms required to mitigate them,” the non-profit said
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Hackers very frequently target the finance and insurance sectors due to the large volumes of sensitive data that they own.
These areas manage huge quantities of valuable as well as critical financial information, personal identities, and intellectual property.
When their system is breached, threat actors may be able to access bank accounts or credit card details and other key exploitable information to manipulate it for financial gain through extortion or fraud.
Moreover, considerable ransom requests can be made using these critically important areas where their operations are interfered with.
Cybersecurity researchers at Resilience recently discovered that Scattered Spider has been actively attacking the finance and insurance industries worldwide.
Scattered Spider
The Scattered Spider, a group of hackers that has gained fame from breaching the likes of MGM and Caesars Casino, has now widened its attack to insurance companies and banks.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
For instance, they may use misleading domains that are almost indistinguishable from the real ones, timed to strike at the most opportune time and use forceful aggressive attacks that last for only a few hours.
They even go as far as swapping SIM cards to gain remote control over targeted systems consequently emphasizing the urgency for robust impersonation defenses against phishing and credential thefts.
BlackCat (also known as AlphV), which is an affiliate of some other relentless group in no way loses its threatening quality with more than 30 victims so far in government agencies, this means defenders should be more vigilant.
Scattered Spider, the Advanced Persistent Threat group, has been pursuing attacks motivated by finances since 2022.
For SIM-swapping capabilities, this bold rival first targeted telecommunications companies before going ahead to contact victims directly in an effort to get socially engineer access.
By 2023, they had switched their focus to partnering with BlackCat ransomware creators making it possible to successfully breach Caesars Entertainment and MGM Resorts which are some of the most important targets.
There is a recent strategy change in Scattered Spider’s campaigns which now involve an intricate selection process that only goes for high-value organizations on the corporate level instead of taking advantage of any available target.
These crafty groups’ multi-tiered tactics still keep telecom providers at the inlet, which necessitates constant alertness, reads the Resilience Report.
Scattered Spider has the bold strategy of buying look-alike domains to impersonate victims such as “victimname-sso.com” where they host fake Okta login pages.
.webp)
telynyx Okta phishing site (Source – Resilience) These phishing sites have uncouth fingerprints, a “Need help?” that links to a real Okta subdomain but with a wrong name, and form submissions going towards “/f*ckyou.php.”
Believed to be part of Star Fraud or The Com hacker community notorious for their illicit actions, Scattered Spider is said to have used an offending named Telegram channel in data extraction.
.webp)
Charter Communications Okta phishing page (Source – Resilience) Starting by targeting telecoms initially, this group has gone rogue into food, insurance, retail, technology, and gaming industries as shown by their recent attack on Charter Communications using charter-vpn.com domains.
.webp)
Asurion CMS phishing page and Asurion Okta phishing page (Source – Resilience) Scattered Spider has been identified with a spearfishing campaign that exploited lookalike domains, and fraudulent CMS login pages titled “CMS Dashboard Login” masquerading as Okta campaigns and lasted for 12-48 hours before targeting the same organizations.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for FreeThe post Scattered Spider Attacking Finance & Insurance Industries WorldWide appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Tycoon 2FA, a recently emerged Phishing-as-a-Service (PhaaS) platform, targets Microsoft 365 and Gmail accounts, which leverage an Adversary-in-the-Middle (AitM) technique to steal user session cookies, bypassing multi-factor authentication (MFA) protections.
By acting as an intermediary between the user and the legitimate login page, Tycoon 2FA captures cookies that grant attackers unauthorized access to compromised accounts and cloud services, even if additional security measures are implemented.
The Tycoon 2FA phishing kit received an update in March 2024, specifically designed to bypass security defenses, and the update enhanced the kit’s evasion capabilities through obfuscated JavaScript and HTML code, making the code unreadable, hindering analysis.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
Additionally, the update incorporated dynamic code generation, meaning the code rewrites itself upon each execution, which allows the kit to avoid detection by signature-based security systems.
.webp)
Tycoon 2FA to facilitate MFA token theft and bypass. On Telegram, it sells pre-made phishing pages targeting Microsoft 365 and Gmail credentials, which lowers the technical barrier for attackers by offering easy-to-use templates.
.webp)
Proofpoint TAP Dashboard campaign snapshot from December campaigns. The attack works through a reverse proxy, capturing login credentials and relaying them to the real service to bypass the login page, as the attackers steal the session cookies returned during successful logins, granting unauthorized access even with MFA enabled.
It facilitates credential theft by bypassing multi-factor authentication (MFA), and attackers use various lures such as emails with fake authentication links, voicemail-themed threats, and PDFs with QR codes leading to phishing pages.
.webp)
QR code and voicemail lure examples for the Tycoon 2FA threats that were seen in late 2023. The pages often include CAPTCHAs to appear legitimate and steal login credentials and MFA tokens. Security researchers at Proofpoint identified rules to detect Tycoon landing pages based on these tactics.
AI-powered behavioral analytics and a URL sandbox are used to identify and block malicious landing pages and phishing activity associated with Tycoon 2FA and similar threats that are achieved by combining threat intelligence with machine learning to recognize suspicious behaviors.
Global threat intelligence feeds give information about bad infrastructure, which helps defenders stop known and new threats before they happen by making it easier to find them, fix problems, and manage human risk when it comes to new phishing techniques.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for FreeThe post Tycoon 2FA Attacking Microsoft 365 AND Google Users To Bypass MFA appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cacti, the widely utilized network monitoring tool, has recently issued a critical security update to address a series of vulnerabilities, with the most severe being CVE-2024-25641.
This particular vulnerability has been assigned a high severity rating with a CVSS score of 9.1, indicating its potential impact on affected systems.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackersCVE-2024-25641– Critical RCE Vulnerability
CVE-2024-25641 allows authenticated users with the “Import Templates” permission to execute arbitrary PHP code on the server hosting the Cacti application.
The vulnerability stems from improper sanitization and validating file names and content within uploaded XML data in the import_package() function.
This flaw could lead to arbitrary file writes on the web server. Security researcher Egidio Romano has demonstrated the exploitability of this vulnerability through a proof-of-concept PHP script.
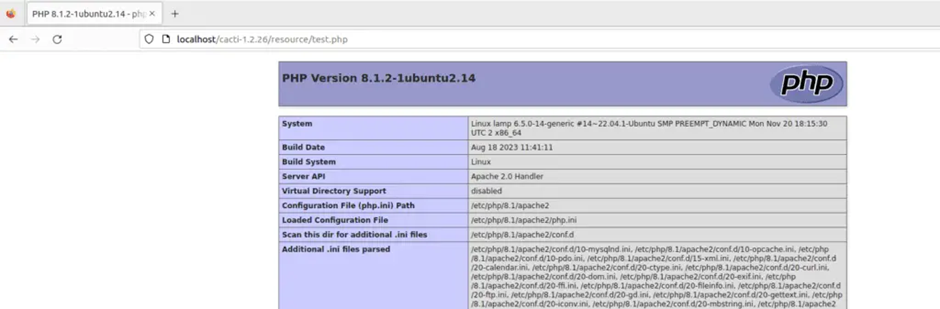
Vulnerability through a proof-of-concept PHP script. This script showcases how attackers can easily manipulate the import process to inject and execute malicious code, thereby gaining unauthorized access to the system.
Additional Vulnerabilities and Fixes
In addition to CVE-2024-25641, the latest Cacti update addresses several other security issues:
- CVE-2024-34340 (CVSS 4.2): An authentication bypass issue due to older password hashes, potentially allowing unauthorized access.
- CVE-2024-31443 (CVSS 5.7) and CVE-2024-27082 (CVSS 7.6): These vulnerabilities relate to XSS flaws that could enable attackers to inject client-side scripts into web pages and manipulate sessions.
- CVE-2024-31444, CVE-2024-31458, CVE-2024-31460, and CVE-2024-31445 (ranging from CVSS 4.6 to 8.8): A series of SQL injection flaws that could allow attackers to alter the framework’s database queries, leading to unauthorized data manipulation or access.
- CVE-2024-31459: An RCE vulnerability linked to file inclusion via plugins, which could allow the execution of arbitrary code.
- CVE-2024-29894: An XSS vulnerability in the JavaScript-based messaging API exploitable for executing malicious scripts.
These vulnerabilities vary in severity, with potential impacts ranging from cross-site scripting (XSS) attacks to SQL injection and arbitrary code execution.
With technical details and proof-of-concept code for these vulnerabilities now public, the urgency for Cacti users to update their systems cannot be overstated.
All platform users are strongly encouraged to upgrade to version 1.2.27 or later as soon as possible to mitigate the risks associated with these vulnerabilities.
The release of these patches highlights the ongoing challenges and the critical importance of maintaining up-to-date security practices in network monitoring tools like Cacti.
Users must remain vigilant and proactive in applying security updates to protect their networks from potential threats.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for FreeThe post Critical Cacti Vulnerability Let Attackers Execute Remote Code appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
With the browser becoming the most prevalent workspace in the enterprise, it is also turning into a popular attack vector for cyber attackers. From account takeovers to malicious extensions to phishing attacks, the browser is a means for stealing sensitive data and accessing organizational systems. Security leaders who are planning their security architecture
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Nmap’s version 7.95 emerges as a testament to the relentless efforts of its development team, spearheaded by the renowned Gordon Fyodor Lyon.
The update showcases the remarkable processing of over 6,500 new OS and service detection fingerprints, underscoring the tool’s commitment to staying abreast of the rapidly changing digital landscape.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers“We finally tackled our backlog of OS and service detection fingerprint submissions.
We’re not talking about dozens or hundreds of them – we processed more than 6,500 fingerprints,” stated Lyon, reflecting on the monumental task.
Introducing 336 new signatures expands Nmap’s detection capabilities to 6,036, covering various operating systems and services.
This update includes support for the latest iterations of iOS (versions 15 & 16), macOS (Ventura & Monterey), Linux (version 6.1), OpenBSD (version 7.1), and lwIP (version 2.2), ensuring comprehensive coverage of the most current technologies.
Nmap’s service/version detection feature has also received a significant boost, with the signature count rising by 1.4% to 12,089.
This enhancement includes adding 9 new soft matches, further refining the tool’s ability to identify services and their versions accurately.
The update now supports detecting 1,246 protocols, incorporating new entries such as grpc, myself, asset, remote mouse, and tuya, thereby expanding its utility in diverse network environments.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for FreeThe post Nmap 7.95 released – What’s New! appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A zero-day vulnerability in Microsoft Edge, which has been tagged as CVE-2024-4671, has been aggressively exploited by evil organizations, according to reports.
This security flaw originates from the Chromium engine that underpins the browser. Chromium is also the foundation for Google Chrome and several other similar browsers.
CVE-2024-4671: A Critical Security Breach
As a vulnerability that falls under the “use after free” category, CVE-2024-4671 was formally made available to the public on May 10, 2024.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackersIt is located in the Visuals component of Chromium. An application is said to be experiencing “use after free” problems when it continues to use a memory pointer after it has been freed.
This can result in the execution of arbitrary code.
Because of this, it is a powerful vector that attackers can use to gain maybe control of an impacted machine.
People who use Microsoft Edge and possibly other browsers based on Chromium are at a major risk because it has been established that the exploit for this vulnerability is currently operational in the wild.On the victim’s computer, the attackers can take advantage of this vulnerability to execute malicious code without the victim’s knowledge, which could result in data loss, malware installation, and other malicious activities.
Response from Tech Giants
The Chromium project is managed by Google, which has admitted that the attack exists and is most likely working on a patch to address the vulnerability.
Microsoft will need to hasten a security upgrade to safeguard its users because it receives updates and security fixes from Chromium for its Edge browser.
Microsoft is responsible for ingesting these updates and fixes.
Users should proceed cautiously until a security patch is available to the public. Be mindful of downloading files that are not requested, and steer clear of unknown or untrustworthy websites.Businesses that use Microsoft Edge are strongly encouraged to implement additional security measures and closely monitor network traffic for any odd activities.
The cybersecurity community is on high alert since this vulnerability has the potential to affect a large number of users all over the world.This is due to the broad adoption of browsers based on Chromium code.
Enterprises and individual users must stay current with the most recent security bug updates released by Microsoft and Google.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for FreeThe post Microsoft Edge Zero-Day Vulnerability Exploited in the Wild appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In the last decade, there has been a growing disconnect between front-line analysts and senior management in IT and Cybersecurity. Well-documented challenges facing modern analysts revolve around a high volume of alerts, false positives, poor visibility of technical environments, and analysts spending too much time on manual tasks. The Impact of Alert Fatigue and False Positives Analysts
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cybersecurity researchers have disclosed multiple security flaws in Cinterion cellular modems that could be potentially exploited by threat actors to access sensitive information and achieve code execution. “These vulnerabilities include critical flaws that permit remote code execution and unauthorized privilege escalation, posing substantial risks to integral communication networks and IoT
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The Black Basta ransomware-as-a-service (RaaS) operation has targeted more than 500 private industry and critical infrastructure entities in North America, Europe, and Australia since its emergence in April 2022. In a joint advisory published by the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), the Department of Health and Human Services (HHS
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


