-
It comes as no surprise that today’s cyber threats are orders of magnitude more complex than those of the past. And the ever-evolving tactics that attackers use demand the adoption of better, more holistic and consolidated ways to meet this non-stop challenge. Security teams constantly look for ways to reduce risk while improving security posture, but many
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Multiple critical security flaws have been disclosed in the Judge0 open-source online code execution system that could be exploited to obtain code execution on the target system. The three flaws, all critical in nature, allow an “adversary with sufficient access to perform a sandbox escape and obtain root permissions on the host machine,” Australian
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Microsoft released multiple product security patches on their April 2024 Patch Tuesday updates.
One of the vulnerabilities addressed was CVE-2024-26218, associated with the Windows Kernel Privilege Escalation vulnerability, which had a severity of 7.8 (High).
This vulnerability relates to a TOCTOU (Time-of-Check Time-of-Use)Race Condition that could be exploited.
Successful exploitation of this vulnerability could allow a threat actor to gain SYSTEM privileges.
This vulnerability existed in multiple versions of Windows 10, Windows 11, and Windows Server (2019, 2022).
However, Microsoft has patched this vulnerability, and users are advised to update their Operating Systems accordingly.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideTechnical Analysis
A proof of concept for this vulnerability has been published in GitHub which consists of a DEF file, a EXP file, a LIB file and an SLN file.
Additionally, another folder was found on the repository, which had a C file, a VCXPROJ file, and a VCXPROJ filters file.
On investigating further, an explanation of this vulnerability was provided by the researcher who discovered this proof of concept.
The explanation suggests that this vulnerability exists due to a double fetch performed by the PspBuildCreateProcessContext function in Windows.
When creating a process, multiple attributes are created and provided to NtCreateUserProcess syscall via PS_ATTRIBUTE_LIST, an array of PS_ATTRIBUTE structures.
This list of attributes will reside in the user mode memory which are then processed by the PspBuildCreateProcessContext function.
As a matter of fact, this function contains a large number of scenarios for handling every attribute type it processes.
On looking deep into it, it was discovered that this PspBuildCreateProcessContext function performs a double-fetch of the Size field when handling the PsAttributeMitigationOptions and PsAttributeMitigationAuditOptions attribute types.
This is where the race condition exists in which the value of the Size field can be changed between the fetches that could potentially result in a stack buffer overflow.
Though this vulnerability has a proof of concept code in GitHub, there is no explanation of exploitation provided.
.webp)
Windows 23H2 edition code (Source: Exploit for Sale) .webp)
Windows 24H2 Edition code (Source: Exploit for Sale) Affected Products And Fixed In Versions
Product Fixed in Build Number Windows 10 Version 22H2 for 32-bit Systems 10.0.19045.4291 Windows 10 Version 22H2 for ARM64-based Systems 10.0.19045.4291 Windows 10 Version 22H2 for x64-based Systems 10.0.19045.4291 Windows Server 2022, 23H2 Edition (Server Core installation) 10.0.25398.830 Windows 11 Version 23H2 for x64-based Systems 10.0.22631.3447 Windows 11 Version 23H2 for ARM64-based Systems 10.0.22631.3447 Windows 11 Version 22H2 for x64-based Systems 10.0.22621.3447 Windows 11 Version 22H2 for ARM64-based Systems 10.0.22621.3447 Windows 10 Version 21H2 for x64-based Systems 10.0.19044.4291 Windows 10 Version 21H2 for ARM64-based Systems 10.0.19044.4291 Windows 10 Version 21H2 for 32-bit Systems 10.0.19044.4291 Windows 11 version 21H2 for ARM64-based Systems 10.0.22000.2899 Windows 11 version 21H2 for x64-based Systems 10.0.22000.2899 Windows Server 2022 (Server Core installation) 10.0.20348.2402 Windows Server 2022 10.0.20348.2402 Windows Server 2019 (Server Core installation) 10.0.17763.5696 Windows Server 2019 10.0.17763.5696 Windows 10 Version 1809 for ARM64-based Systems 10.0.17763.5696 Windows 10 Version 1809 for x64-based Systems 10.0.17763.5696 Windows 10 Version 1809 for 32-bit Systems 10.0.17763.5696 It is recommended that users of these vulnerable versions upgrade to the latest versions to prevent threat actors from exploiting this vulnerability.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post PoC Exploit Released For Windows Kernel EoP Vulnerability appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A large botnet-as-a-service network originating from China was discovered, which comprises numerous domains, over 20 active Telegram groups, and utilizes other domestic communication channels.
The infrastructure that supports this botnet, located in China, raises concerns about the potential for large-scale, coordinated attacks. Botnets are collections of compromised devices that attackers can remotely control.
The attackers can then use the botnet’s combined processing power to disrupt operations, steal data, or launch denial-of-service attacks that overwhelm targeted systems with traffic, rendering them inaccessible to legitimate users.
Even if a target is using these well-known DDoS protection services, it is still at risk of being offline due to a denial-of-service attack because a group has developed strategies and a botnet that can bypass the most recent DDoS protection solutions from CloudFlare and other vendors.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe technical particulars of how the methods and botnets operate are not known to the general public; however, it is evident that they are successful in evading the defenses that are currently in place.
Malicious actors within online groups target European companies’ domain names across various sectors, which act as unique identifiers for company websites and online presence.
By compromising these domains, attackers could potentially redirect users to fraudulent websites designed to steal data or spread malware, highlighting the Domain Name System (DNS) vulnerability. This infrastructure translates domain names into IP addresses.
Protecting these domains and implementing stringent DNS security measures is absolutely necessary for European businesses to safeguard their online operations and customers’ trust.
.webp)
Screenshot of one of the channel A report by EPCYBER alleges that a website was able to launch a DDoS attack against itself, successfully bypassing CloudFlare’s latest DDoS protection measures by raising concerns about a potential vulnerability in CloudFlare’s system.
DDoS attacks work by overwhelming a target system with a deluge of traffic, rendering it inaccessible to legitimate users.
CloudFlare typically mitigates DDoS attacks by filtering out malicious traffic before it reaches the target website.
However, it suggests that the attacker may have identified and exploited a loophole in CloudFlare’s recent DDoS rule updates, and this loophole allowed the attacker’s DDoS traffic to bypass CloudFlare’s filters and reach the target website, ultimately causing a successful DDoS attack.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Chinese Botnet As-A-Service Bypasses Cloudflare & Other DDoS Protection Services appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new ransomware named KageNoHitobito has been targeting Windows users across various countries.
It encrypts their data and demands a ransom through sophisticated means.
This article delves into the mechanics of the KageNoHitobito ransomware and its attack methodology and provides a brief overview of another emerging threat, the DoNex ransomware.
Infection Vector/Victimology
The KageNoHitobito ransomware has been identified in multiple countries, including Chile, China, Cuba, Germany, Iran, Lithuania, Peru, Romania, Sweden, Taiwan, the United Kingdom, and the United States.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe widespread distribution suggests that the ransomware may have been disseminated through file-sharing services, masquerading as legitimate software or game cheats.
Thus, users were tricked into downloading and executing malicious files.
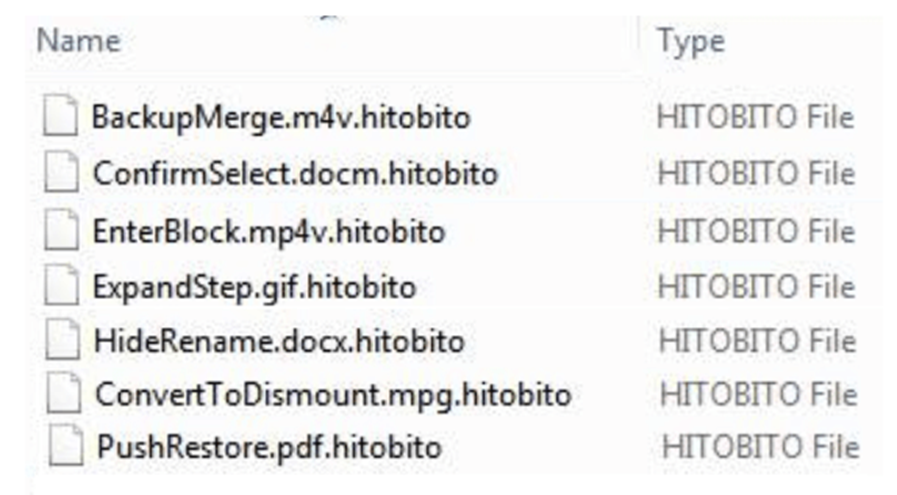
Files encrypted by the KageNoHitobito ransomware According to a recent report by Fortinet, KageNoHitobito ransomware is targeting Windows users across the globe.
The attack is designed to exploit Windows system vulnerabilities, leading to compromised security and potential data loss.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Attack Method
KageNoHitobito is designed to encrypt files on local drives, appending a “.hitobito” extension to the encrypted files.
It strategically avoids encrypting critical system files such as .dat, .dll, .exe, .ini, .log, and .sys to ensure the system remains operational, presumably to facilitate communication with the victim for ransom negotiations.
The ransomware displays a ransom note on the victim’s desktop and drops a text-based note, urging victims to contact the attackers via a TOR site using the AbleOnion chat platform.
Interestingly, the chat platform does not seem dedicated solely to ransom negotiations, indicating a possible use of a public or shared platform to avoid detection.
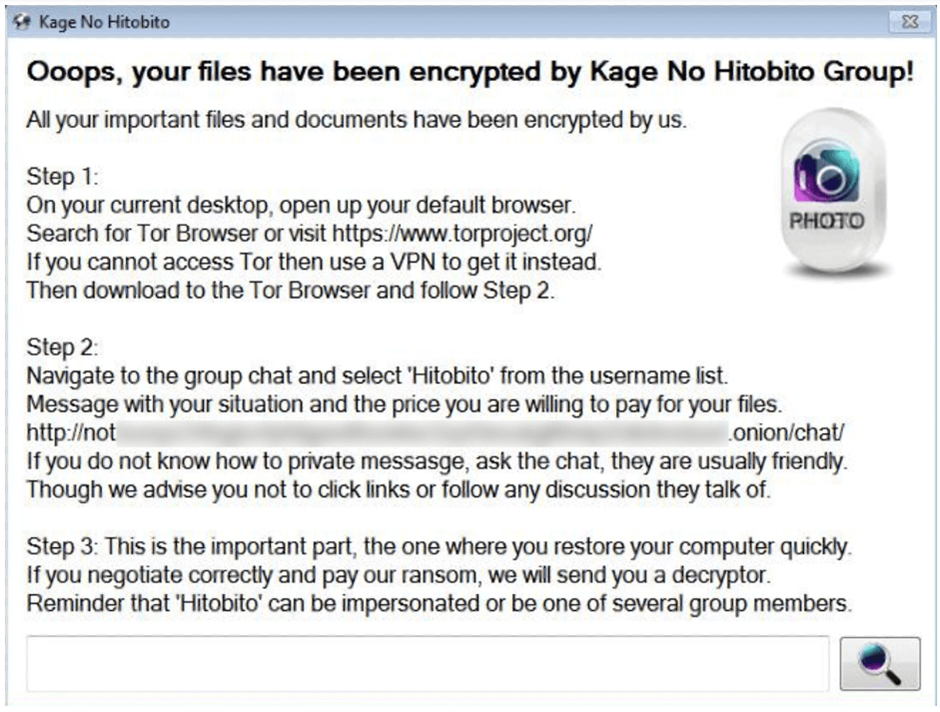
KageNoHitobito ransomware’s ransom note displayed on the victim’s desktop DoNex Ransomware Overview
Parallel to the KageNoHitobito, another ransomware named DoNex has been making rounds since early March 2024.
Unlike KageNoHitobito, DoNex has a data leak site and has been reported to encrypt files on both local and network drives.
The ransomware is highly configurable, allowing it to adapt its operations based on the environment it infects.
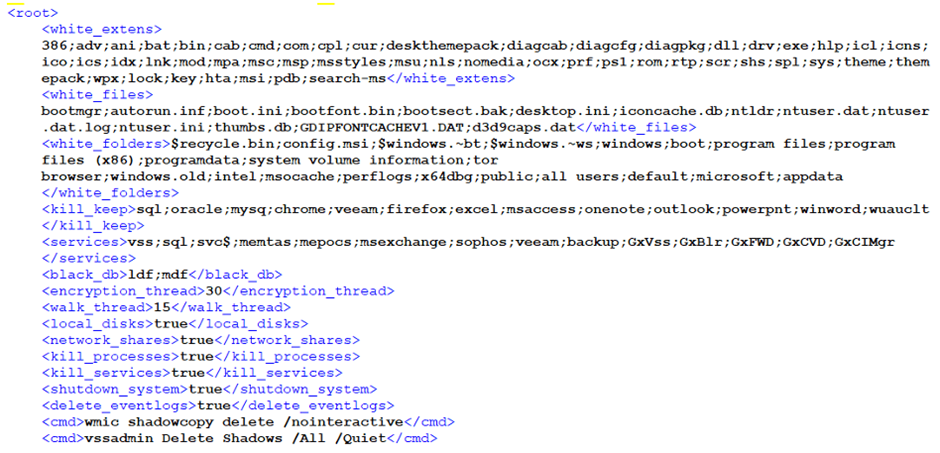
DoNex ransomware’s configuration file DoNex avoids encrypting a wide range of file extensions and specific critical system folders, ensuring the system’s usability post-infection.
It also terminates various processes and services, enhancing its ability to encrypt files without interference.
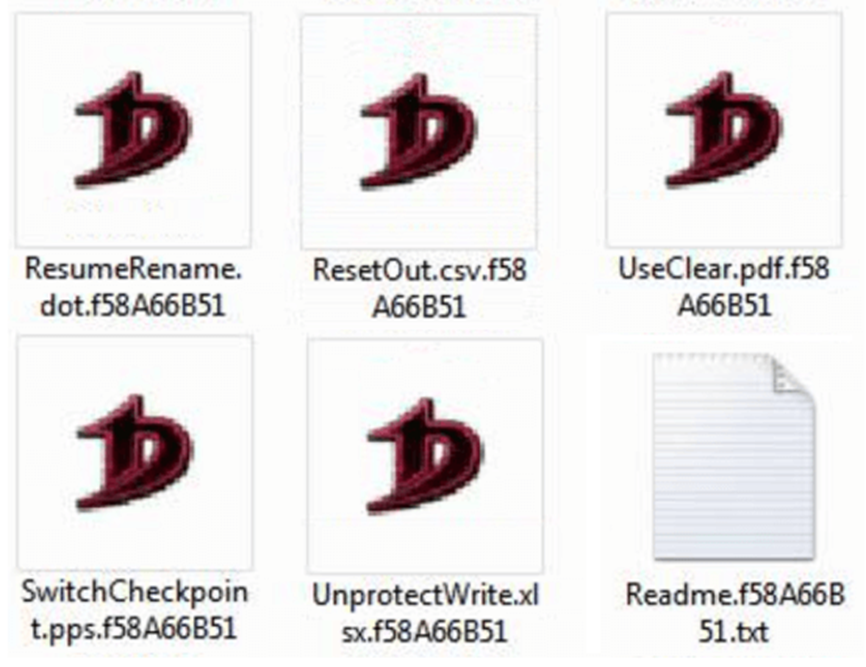
Files encrypted by the DoNex ransomware The ransom note of DoNex shares similarities with another ransomware, DarkRace, suggesting a possible link between the two in terms of their origin or the threat actors behind them.
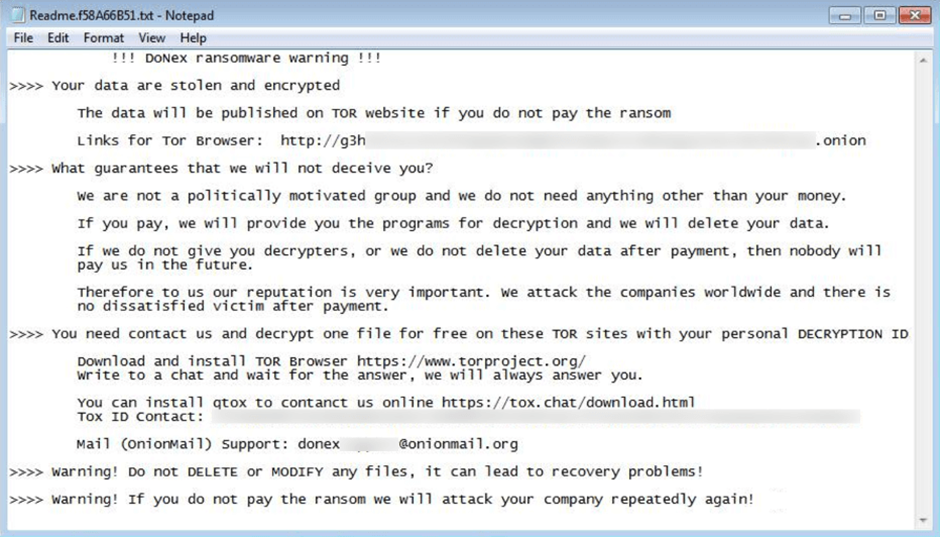
The DoNex ransomware’s ransom note Both KageNoHitobito and DoNex ransomware represent significant threats to global cybersecurity.
Their sophisticated attack methods and international reach highlight the need for increased vigilance and robust cybersecurity measures among users and organizations worldwide.
IOCs
SHA2 Note 8939bfe20bc6476806d22c8edfcaba5c36f936b893b3de1c847558502654c82f Hitobito ransomware 1940fcdb2561c2f7b82f6c44d22a9906e5ffec2438d5dadfe88d1608f5f03c33 506e8753dd5ca1c8387be32f26367e26f242b7c65e61203f7f926506c04163aa 8a10e0dc4994268ea33baecd5e89d1e2ddabef30afa09961257a4329669e857a bec9d2dcd9565bb245f5c8beca4db627390bcb4699dd5da192cc8aba895e0e6a 0adde4246aaa9fb3964d1d6cf3c29b1b13074015b250eb8e5591339f92e1e3ca DoNex ransomware 6d6134adfdf16c8ed9513aba40845b15bd314e085ef1d6bd20040afd42e36e40 b32ae94b32bcc5724d706421f915b7f7730c4fb20b04f5ab0ca830dc88dcce4e 74b5e2d90daaf96657e4d3d800bb20bf189bb2cf487479ea0facaf6182e0d1d3 DarkRace ransomware(predecessor of DoNex) 0e60d49a967599fab179f8c885d91db25016be996d66a4e00cbb197e5085efa4 Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post KageNoHitobito Ransomware Attacking Windows Users Around the Globe appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Hackers often focus on flaws in Microsoft products since they are commonly employed in various institutions and personal computers, which means they have a bigger area to attack.
This is because these systems could be used as an entry point into sensitive information, letting attackers take over or spread malicious software and malware without permission.
Cybersecurity researchers at BeyondTrust recently detected over 1200 vulnerabilities in Microsoft products in 2023.
Technical Analysis
In 2023 alone, the company still had to address 522 problems with Windows (55 of them critical), 249 with Edge, 92 with Office, and 558 with Windows Server (57 of them critical) — although those numbers were down from their heights in 2022.
However, there was also an alarming surge in new types of vulnerabilities, and the Denial of Service flaws grew by more than half to 109.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoSpoofing vulnerabilities skyrocketed by nearly four times from 31 to 90, pointing to new attack vectors even as overall vulnerability disclosures dropped.
Totals remained flat for four years following Microsoft’s vulnerability peak in 2020, fluctuating within 7% of one another before settling at 1228 in 2023; it’s a 5% decrease from the record high of 1292 set in 2022, according to the report.
This flat was brought about by retiring the legacy products predating Microsoft’s Security Development Lifecycle, which were replaced with newer, more secure offerings.
Though not as significant as previous years’ declines, the continued fall is still good news for IT professionals encouraged by this trend.
The likelihood of successful exploitation varies greatly depending on how widely known and understood any given flaw may be among potential attackers.
So, the overall counts only indicate environmental robustness rather than reflecting entire risk landscapes.
While the National Vulnerability Database marked 33 Microsoft flaws in 2023 as critical (9.0+ score), a 50% increase from 2022, Microsoft classified 84 as critical, down 6%.
Elevation of Privilege remained the top vulnerability category despite a 31% drop to 490, followed by Remote Code Execution’s 13% rise to 356, partly offset by Azure, Office, and Windows declines.
The RCE increase in Windows Server resulted from Microsoft’s collaboration with security researchers, disclosing and patching flaws before public exploitation.
Browser and document viewer vulnerabilities declined as Edge adopted Chromium’s matured security, and dropping Internet Explorer eliminated drive-by downloads and Flash exploits.
Critical Edge vulnerabilities dived from 162 in 2017 to just 1 in 2023, presenting Chromium’s hardened security benefits.
While up in 2023, Office vulnerability totals show a long-term downward trend as older versions reach End-of-Life, forcing attackers to innovate past mitigations like disabling auto-run macros.
However, adding SketchUp 3D file support introduced 117 new vulnerabilities that bypassed initial patches, temporarily disabling the feature.
Mitigations
Here below we have mentioned all the mitigations offered by the cybersecurity researchers:-
- Enforce the least privilege by removing local admin rights
- Follow security hardening protocols7 such as patching
- Secure remote access pathways
- Tailor vulnerability management to your own environment
- Stay vigilant to emerging threats
- Implement identity threat detection and response (ITDR)
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post 1,200+ Vulnerabilities Detected In Microsoft Products In 2023 appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Okta has issued a warning about the increasing prevalence of credential-stuffing attacks.
These attacks, which leverage stolen user credentials to gain unauthorized access to accounts, are facilitated by the widespread use of residential proxy services.
This alarming trend underscores the evolving challenges in cybersecurity and highlights the need for robust defensive measures.
The Rise of Credential Stuffing Attacks
From mid-March to late April 2024, cybersecurity teams at Duo Security, Cisco Talos, and Okta’s own Identity Threat Research team have observed a significant uptick in brute force and credential stuffing attacks.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThese attacks are becoming more frequent and sophisticated, utilizing advanced tools and the anonymity provided by proxy services like TOR, NSOCKS, Luminati, and DataImpulse.
Credential stuffing attacks involve using large databases of usernames and passwords—acquired through previous data breaches, phishing, or malware campaigns—to attempt logins on various online platforms.
These recent attacks are particularly concerning because they rely on residential proxies, which use legitimate user devices to disguise the attackers’ origins, making the attacks more challenging to detect and trace.
Understanding Residential Proxies
Residential proxies are networks that route internet traffic through real users’ devices to anonymize the source.
These proxies can be a double-edged sword.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
On the one hand, they provide valuable services like content localization and ad verification; conversely, they can be exploited for malicious activities like credential stuffing.
Deploying residential proxies often involves “proxyware” voluntarily installed by users or, more maliciously, through malware and compromised mobile apps.
This latter method enrolls devices into a botnet-like network without the owner’s knowledge, using them as conduits for illegal activities.
Okta’s Proactive Measures and Recommendations
In response to these threats, Okta has proactively enhanced its security features.
Earlier this year, Okta introduced a new capability in its Workforce Identity Cloud (WIC) and Customer Identity Solution (CIS) that detects and blocks requests from anonymizing services.
Block Requests This feature is part of Okta’s broader strategy to implement default security measures that protect against such vulnerabilities.
For organizations using Okta’s services, the following measures are recommended:
- Enable the Early Access feature to block anonymizing proxies directly from the Okta Admin Console.
- Use Dynamic Zones for more granular control over which anonymizers are blocked.
- Consider upgrading the Okta Identity Engine for additional features like CAPTCHA challenges and passwordless authentication with Okta FastPass.
Furthermore, Okta advises all its customers to adopt a defense-in-depth approach.
This includes enabling ThreatInsight in log and enforce mode, which has proven effective in blocking IPs associated with high-volume credential-based attacks.
As cyber threats continue to evolve, staying ahead of attackers requires not only the use of advanced technological solutions but also a comprehensive understanding of the tactics employed by cybercriminals.
Okta’s ongoing efforts to enhance security and educate its users are vital in fighting credential stuffing and other forms of cyber aggression.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Okta Warns of Credential Stuffing Attacks Using Proxy Services appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new family of mobile malware known as “Brokewell” has been found to have a wide range of device takeover capabilities.
This seriously threatens the banking sector by giving attackers remote access to all the resources made available via mobile banking.
New instructions introduced virtually every day indicate the Trojan is still under development.
Experts say Brokewell will most likely be offered as a rental service through underground channels, receiving the attention of other cybercriminals and inspiring new operations targeting different regions.
“These actors require this functionality to commit fraud directly on victims’ devices, creating a significant challenge for fraud detection tools that heavily rely on device identification or device fingerprinting,” ThreatFabric researchers shared with Cyber Security News.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideBrokewell’s Primary Features
Researchers discovered a fake browser update page intended to install an Android application.
This strategy appears innocent to unwary victims—with a skillfully designed website offering an update for a more recent version of the program—and normal—as it happens during regular browser use.
According to researchers, the downloaded application is a family of malware with unprecedented capabilities.
.webp)
Fake page distributing Brokewell Brokewell is a classic example of contemporary banking malware that can remotely operate itself and steal data.
Overlay attacks, a popular method for Android banking malware, are employed by Brokewell to obtain user credentials by combining a fake screen over a targeted application.
Brokewell can also steal cookies, another characteristic common to modern mobile banking malware.
It accomplishes this by loading the authentic webpage, overriding the onPageFinished method, and starting its own WebView.
After the victim successfully logs in, Brokewell dumps the session cookies and sends them to the command and control (C2) server.
.webp)
Stealing victim’s credentials With its “accessibility logging,” Brokewell records all user interactions, including touches, swipes, information displays, text input, and programs opened.
Any private information typed or seen on the infected device is effectively stolen because every action is recorded and transmitted to the command-and-control server.
After obtaining the credentials, the actors can use remote control capabilities to launch a Device Takeover attack.
To do this, the malware streams the screen and gives the actor access to various commands that can be used on the device under control, including touches, swipes, and clicks on designated elements.
“These capabilities might be further expanded in the future by automating specific actions to streamline the Device Takeover attack for the actors and potentially create a functional Automated Transfer System (ATS)”, researchers said.
A New Actor In The Field Of Mobile Malware
Brokewell was used to host a repository named “Brokewell Cyber Labs,” created by “Baron Samedit.”
Researchers say source code for “Brokewell Android Loader,” another tool created by the same developer to bypass Android 13+ are limitations on Accessibility Service for side-loaded apps, is available in this repository.
.webp)
Threat actor advertises their products, including mobile threats and other offerings Hence, the only way to properly identify and stop potential fraud from malware families like the recently identified Brokewell is to use a comprehensive, multi-layered fraud detection solution that is based on a combination of indicators, including device behavior and identity threats for each customer.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Android Malware Brokewell With Complete Device Takeover Capabilities appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A recent malware campaign used a VBA macro in a Word document to download and execute a 64-bit Rust binary. This binary employs fileless injection techniques to load a malicious AgentTesla payload into its memory space.
The malware leverages CLR hosting, a mechanism for native processes to execute.NET code, to achieve this, and the.NET runtime libraries are loaded dynamically, allowing the malware to operate without writing files to disc.
The malware disables Event Tracing for Windows (ETW) by patching the “EtwEventWrite” API and then downloads a shellcode containing the AgenetTesla payload from a specific URL. The shellcode is then executed using the “EnumSystemLocalesA” API.
After the malware patches, the “EtwEventWrite” API The shellcode uses hashing to dynamically resolve APIs like VirtualAlloc, VirtualFree, and RtlExitUserProcess so that it does not get caught, and then allocates memory and writes the decoded AgentTesla payload to that memory so that it can be run.
Moved shellcode from read-write memory to executable memory and started its execution To begin, the malware gets the size and encoded shellcode data from memory. It then uses a custom decryption routine that decrypts 0x10 byte chunks of the payload one at a time using a different dynamically generated 0x10 byte key each time.
Document Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Single-byte XOR decryption If a required DLL is missing, the malware utilizes LoadLibraryA to load it, and the shellcode leverages API hashing to locate functions like VirtualProtect, SafeArrayCreate, and CLRCreateInstance within the loaded libraries.
The shellcode disables AMSI scanning by patching the “AmsiScanBuffer” and “AmsiScanString” functions in memory, and then performs CLR hosting to execute malicious.NET code.
“AmsiScanBuffer” API after patching It involves creating a CLR runtime instance, enumerating installed runtimes to find a desired .NET version, and retrieving the default AppDomain. A SafeArray is created to hold the malicious assembly bytecode, which is then loaded into the AppDomain. The loaded assembly’s entry point is invoked with any arguments passed through another SafeArray.
According to SonicWall, the shellcode utilizes CLR hosting to execute malicious.NET code (the MSIL AgentTesla payload) in memory and achieves this by first calling CLRCreateInstance to get a CLR MetaHost instance.
Browser folder enumerated by 64-bit process once the fileless managed code injection has been done It retrieves interfaces like ICorRuntimeHost to set up and start the CLR runtime, creates a SafeArray object containing the decrypted MSIL payload, and loads it into the default application domain.
The shellcode calls Invoke_3 to execute the entry point of the loaded assembly, effectively launching the AgentTesla process within the native process. After execution, the shellcode wipes the MSIL payload and destroys the SafeArray object.
IOCs
Document file:
MD5 : D99020C900069E737B3F4AB8C6947375
SHA256 : A6562D8F34D4C25A94313EBBED1137514EED90B233A94A9125E087781C733B37
64-bit downloaded executable:
MD5 : 4521162D45EFC83FA76C4B5C0D405265
SHA256 : F00ED06A1D402ECF760EC92F3280EF6C09E76036854ABACADCAC9311706ED97D
Shellcode blob:
MD5 : CD485BF146E942EC6BB51351FA42B1FF
SHA256 : 02C03E2E8CA28849969AE9A8AAA7FDE8A8B918B5A29548840367F3ECAC543E2D
Injected AgentTesla Payload:
MD5 : 6999D02AA08B56EFE8B2DBBD6FDC9A78
SHA256 : 7B6867606027BFCA492F95E2197A3571D3332D59B65E1850CB20AA6854486B41
URLs used by malware:
https[:]//New-Coder[.]cc/Users/signed_20240329011751156[.]exe (64-bit exe downloaded)
https[:]//New-Coder[.]cc/Users/shellcodeAny_20240329011339585[.]bin (shellcode downloaded)
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Fileless .NET Based Code Injection Attack Delivers AgentTesla Malware appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The PLA axes an organization once hailed as evidence of innovation.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


