-
The U.S. Department of Justice (DoJ) on Wednesday announced the arrest of two co-founders of a cryptocurrency mixer called Samourai and seized the service for allegedly facilitating over $2 billion in illegal transactions and for laundering more than $100 million in criminal proceeds. To that end, Keonne Rodriguez, 35, and William Lonergan Hill, 65, have been charged
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Attackers are employing evasion techniques to bypass detection and extend dwell time on compromised systems. This is achieved by targeting unmonitored devices, leveraging legitimate tools, and exploiting zero-day vulnerabilities.
While defenders are improving detection speed (dwell time decreased from 16 to 10 days), this is partly due to faster ransomware identification and adversary-in-the-middle and social engineering tactics to bypass multi-factor authentication.
Cloud infrastructure is under attack, with attackers even leveraging cloud resources. Both red and purple teams are exploring AI for better security outcomes as they analyze these trends and offer mitigation strategies to the security community.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideIn 2023, more than half of compromised organizations learned of the incident from an external source, most commonly through a ransom demand from the attacker (70% for ransomware-related intrusions).
.webp)
Ransomware External Notification Source, 2023 It suggests improved internal detection capabilities, as the percentage of externally notified intrusions decreased compared to 2022 (54% vs. 63%).
Ransomware events are most often discovered externally (70%), with attacker ransom notes being the dominant notification method (75% of externally discovered ransomware intrusions).
Investigations into ransomware attacks are on the rise again, reaching 23% of all investigations in 2023, surpassing the 2022 numbers and matching the 2021 levels.
Organizations are also becoming faster at detecting ransomware than other intrusions, with a median detection time of just 5 days in 2023.
.webp)
Global Median Dwell Time by Detection Source The improvement is seen across the board, with internal detection dropping to 6 days and external notification leading to a 5-day detection window.
Overall, dwell time (time attackers remain undetected) continues to decrease, highlighting the urgency of rapid response to security incidents.
Mandiant’s 2023 incident response investigations showed financial, business, and professional services, high tech, retail and hospitality, and healthcare as the most targeted industries.
.webp)
Global Industries Targeted, 2023 These sectors hold sensitive data like PII, PHI, and financial information, and the most typical initial infection vector was an exploit (38%), followed by phishing (17%) and prior compromises (15%). This suggests that attackers are increasingly using exploits and leveraging existing network breaches to gain access.
There was a rise in financially motivated cyberattacks in 2023, with ransomware being the most common culprit. Data theft also remained prevalent, though slightly less frequent than in 2022.
In some cases, stolen data was directly sold for extortion, while other attackers used a combination of data theft, ransomware deployment, and extortion threats.
Data breaches involving intellectual property and targeted theft by espionage groups were also identified.
.webp)
Observed Threat Groups by Goal, 2023 They tracked a vast number of threat actors, encountering over 300 unique groups during incident response in 2023. A significant portion (719) were newly identified, with over half exhibiting financial motivations.
It aligns with the rise in ransomware observed in 2023, as espionage and other objectives saw a modest decline, while a substantial number (36%) remains challenging to categorize definitively due to limited evidence.
In 2023, a consistent distribution of malware categories was observed, with backdoors (33%), downloaders (16%), droppers (15%), credential stealers (7%), and ransomware (5%) being the top five.
Credential stealers re-entered the top five in 2023, while ransomware families decreased from 7% in 2022 to 5% in 2023. This suggests a rise in preexisting ransomware strains like LOCKBIT, ALPHV, BASTA, and ROYALLOCKER.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Cyber Attack Defenders Up For Battle: Huge Uptick In Timely Attack Detections appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cisco has released critical security updates to address multiple vulnerabilities in its Adaptive Security Appliance (ASA) devices and Firepower Threat Defense (FTD) software, collectively known as the “ArcaneDoor” vulnerabilities.
If exploited, these vulnerabilities could allow a cyber threat actor to take control of an affected system.
The Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities Catalog, indicating active exploitation in the wild.
Recently, GBHackers on Security reported that a sophisticated cyber espionage campaign dubbed “ArcaneDoor” conducted by a state-sponsored threat actor tracked as UAT4356 to exploit these 2 zero-day vulnerabilities (CVE-2024-20353 and CVE-2024-20359) in Cisco’s Adaptive Security Appliance (ASA) firewalls.
Combat Email Threats with Free Phishing Simulations: Email Security Awareness Training ->Try Free DemoCVE-2024-20353 and CVE-2024-20359: Persistent Remote Code Execution Vulnerabilities
These two vulnerabilities tracked as CVE-2024-20353 and CVE-2024-20359, are persistent remote code execution vulnerabilities in Cisco ASA and FTD software.
They allow an unauthenticated, remote attacker to execute arbitrary code on the underlying operating system with root-level privileges.
The vulnerabilities exist due to improper handling of certain HTTP requests and improper sanitization of user-supplied data.
An attacker could exploit these vulnerabilities by sending crafted HTTP requests to a targeted device, potentially leading to complete system compromise.
“To determine whether a device that is running Cisco ASA Software or FTD Software is affected, use the show asp table socket | include SSL command and look for an SSL listen socket on any TCP port.”
If a socket is present in the output, the device should be considered vulnerable. The following example shows the output for a Cisco ASA device with two SSL listen sockets on TCP port 443 and TCP port 8443:
ciscoasa# show asp table socket | include SSL
SSL 00185038 LISTEN 172.16.0.250:443 0.0.0.0:*
SSL 00188638 LISTEN 10.0.0.250:8443 0.0.0.0:*Cisco has confirmed active exploitation of these vulnerabilities and has released software updates to address them. No workarounds are available, and users are strongly encouraged to apply the necessary updates immediately.
CVE-2024-20358: Web Services Denial of Service Vulnerability
CVE-2024-20358 is a denial of service (DoS) vulnerability in the management and VPN web servers of Cisco ASA and FTD software.
An unauthenticated, remote attacker could cause the affected device to reload unexpectedly, resulting in a DoS condition.
The vulnerability is due to incomplete error checking when parsing an HTTP header.
An attacker could exploit this vulnerability by sending a crafted HTTP request to a targeted web server on the device, causing it to reload and become unavailable.
This vulnerability affects the Cisco ASA restore CLI command that is described in the Software and Configurations chapter of the Cisco ASA Series General Operations CLI Configuration Guide.
This vulnerability does not affect the backup restore functionalities documented in the System Management chapter of the Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager and the Backup and Restore chapter of the Firepower Management Center Configuration Guide.
Cisco has released software updates to address this vulnerability, and there are no workarounds available.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe post Alert! Cisco Releases Critical Security Updates to Fix 2 ASA Firewall 0-Days appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Cybersecurity experts at Seqrite Labs have reported a surge in cyberattacks against Indian government entities.
These attacks have been attributed to Pakistani Advanced Persistent Threat (APT) groups, which have been intensifying their malicious activities.
Attack Methods
The recent campaigns uncovered by Seqrite Labs’ APT team reveal a sophisticated level of cyber warfare.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideThe Pakistani-linked APT group SideCopy has been particularly active, deploying its commonly used AllaKore Remote Access Trojan (RAT) in three separate campaigns.
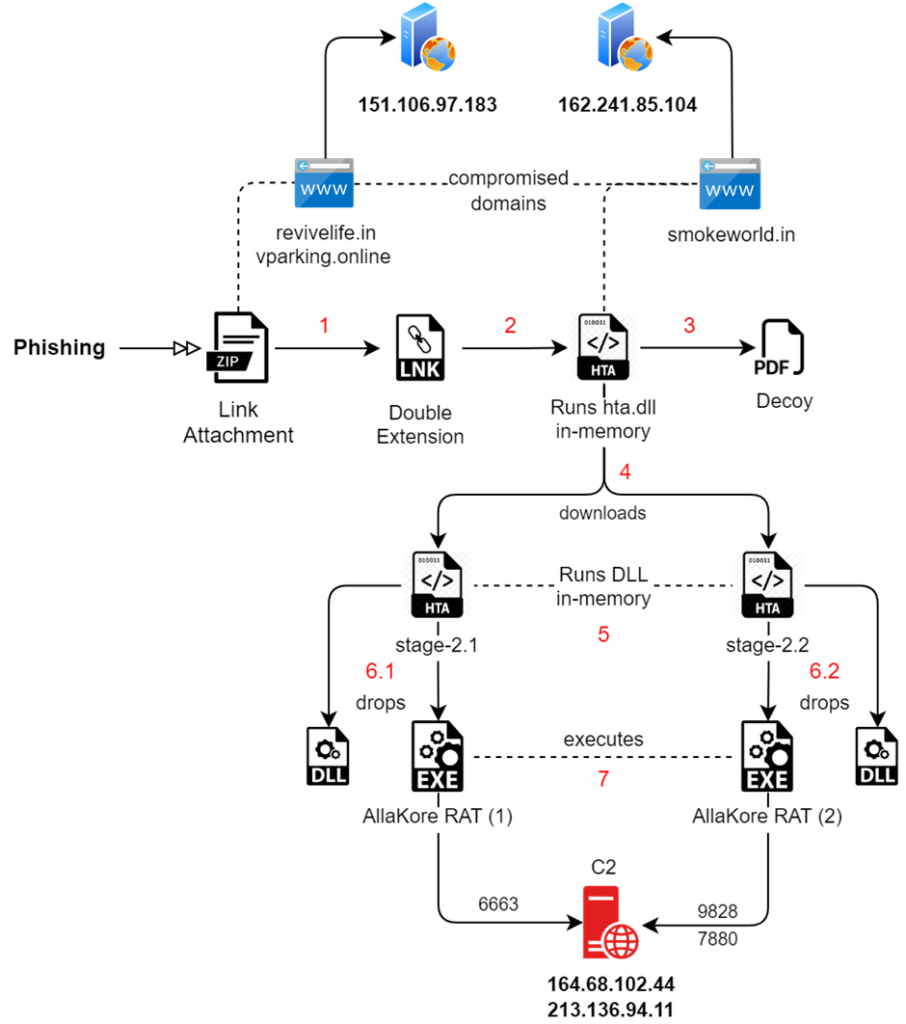
Attack Chain of SideCopy In each of these campaigns, two instances of the RAT were used simultaneously, showcasing the group’s aggressive tactics.
Simultaneously, Transparent Tribe (APT36), the parent group of SideCopy, has been consistently utilizing the Crimson RAT.
However, they have modified their approach by encoding or packing the RAT differently to evade detection.
Targets
The primary targets of these cyberattacks are Indian defense and government entities.
SideCopy and APT36 have been persistent in their efforts to infiltrate these sectors since at least 2019.
The decoy files used in previous campaigns in February-March 2023 have been observed.
“Grant_of_Risk_and_HardShip_Allowances_Mar_24.pdf.” As the name suggests, it is an advisory from 2022 on allowance grants to Army officers under India’s Ministry of Defence.

Decoy Files Their arsenal is not limited to AllaKore and Crimson RATs but includes other malicious tools such as Ares RAT, Action RAT, Reverse RAT, and Margulas RAT.
The impact of these cyberattacks is significant, as they compromise the security and integrity of critical government systems.
The persistent targeting of these entities threatens national security and puts sensitive data at risk of being exploited.
Countermeasures
In response to these escalating threats, Indian cybersecurity forces are urged to strengthen their defenses and remain vigilant.
This includes updating security protocols, conducting regular system checks, and training personnel to effectively recognize and respond to cyber threats.
As geopolitical tensions continue influencing the cyber threat landscape, India remains a prime target for APT groups.
Seqrite Labs’ recent findings underscore the need for robust cybersecurity measures to protect against these sophisticated and persistent threats.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Pakistani APT Hackers Attacking Indian Govt Entities With Weaponized Shortcut Files appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Google has once again pushed its plans to deprecate third-party tracking cookies in its Chrome web browser as it works to address outstanding competition concerns from U.K. regulators over its Privacy Sandbox initiative. The tech giant said it’s working closely with the U.K. Competition and Markets Authority (CMA) and hopes to achieve an agreement by the end of the year. As part of the
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In a joint advisory released by cybersecurity agencies across Canada, Australia, and the United Kingdom, IT professionals and managers in government and critical sectors are alerted to sophisticated cyber-attacks targeting CISCO ASA VPN devices.
Background on the Cyber Threat
The Canadian Centre for Cyber Security and its international counterparts have been monitoring a series of cyber-attacks since early 2024.
These incidents have primarily affected CISCO ASA devices, specifically the ASA55xx series running firmware versions 9.12 and 9.14.
The attacks believed to be espionage efforts by a state-sponsored actor, have not shown signs of prepositioning for a disruptive or destructive network attack.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideHowever, the level of sophistication observed is a cause for concern.
CVE Details and Impact
The first vulnerability identified is CVE-2024-20359, allowing persistent local code execution.
This flaw enables attackers to maintain a presence on the affected device even after it has been rebooted.
The second vulnerability, CVE-2024-20353, can lead to a denial of service within the Cisco Adaptive Security Appliance and Firepower Threat Defense Software’s web services.
This vulnerability could be exploited to disrupt operations and deny access to network resources.
Malicious actors have exploited both vulnerabilities to gain unauthorized access through WebVPN sessions, often associated with Clientless SSLVPN services.
The agencies have not disclosed any specific hacker groups involved, but the capabilities point to a well-resourced and sophisticated actor.
Exploiting these vulnerabilities poses a significant risk to organizations that rely on the affected CISCO ASA VPN devices.
Unauthorized access to these devices can lead to data breaches, espionage, and potentially a foothold for future attacks against critical infrastructure.
Mitigation Strategies
In response to these threats, the advisory encourages organizations to:
- Review logs for unknown, unexpected, or unauthorized device access or changes.
- Update affected devices to the latest firmware versions as soon as possible.
- Visit the Cisco Security Advisories portal and the Cisco Talos Blog for additional information and guidance on mitigation.
- Implement network segmentation and access control lists to limit the traffic allowed to and from the affected devices.
- Employ multi-factor authentication to access VPNs and reduce the risk of unauthorized access.
The alert serves as a reminder of the ever-present cyber threats facing organizations and the importance of maintaining robust cybersecurity practices.
As the situation develops, further updates and recommendations are expected to be issued by the involved cybersecurity agencies.
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training ->Try Free DemoThe post Authorities Warned that Hackers Are Exploiting Flaws in CISCO ASA VPNs appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom malware and facilitate covert data collection on target environments. Cisco Talos, which dubbed the activity ArcaneDoor, attributing it as the handiwork of a previously undocumented sophisticated state-sponsored actor it tracks under the name UAT4356 (aka Storm-1849 by Microsoft). ”
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Security researchers at Cisco Talos have uncovered a sophisticated cyber espionage campaign dubbed “ArcaneDoor” conducted by a state-sponsored threat actor tracked as UAT4356 (STORM-1849).
This campaign targeted government networks globally by exploiting multiple zero-day vulnerabilities in Cisco’s Adaptive Security Appliance (ASA) firewalls.
The attack chain leveraged two custom malware implants – “Line Dancer” and “Line Runner” – to gain persistent access and remote control over compromised ASA devices.
Line Dancer was an in-memory shellcode interpreter that enabled executing arbitrary payloads, while Line Runner provided a persistent backdoor by abusing a legacy VPN client pre-loading functionality.
“Cisco uncovered a sophisticated attack chain that was used to implant custom malware and execute commands across a small set of customers. While Cisco researchers have been unable to identify the initial attack vector, we have identified two vulnerabilities (CVE-2024-20353 and CVE-2024-20359) that were abused in this campaign.”
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free GuideInitial Compromise and Line Dancer Implant
The initial attack vector used to compromise ASA firewalls remains unknown. However, once access was obtained, the hackers deployed the Line Dancer implant – a memory-resident shellcode interpreter.
This allowed them to upload and execute malicious payloads via the host-scan-reply field of the SSL VPN session establishment process.

Line Dancer provided the capability to disable logging, capture device configurations, sniff network traffic, execute CLI commands, and even bypass authentication mechanisms.
It hooked critical functions like crash dumps to hinder forensic analysis and rebooted devices to remove itself from memory.
Persistent Line Runner Backdoor
To maintain access, the hackers exploited two zero-day vulnerabilities (CVE-2024-20353 and CVE-2024-20359) to install the Line Runner persistent backdoor.
This leveraged a legacy feature that allowed pre-loading VPN client bundles on ASAs.
Line Runner consisted of Lua scripts that created a hidden directory, planted a web content file acting as a backdoor, and modified system scripts to copy a malicious ZIP file for execution on every boot.

The threat actor’s ZIP file has the following files: This gave the attackers a persistent HTTP-based backdoor that survived software upgrades and reboots.
Document Integrate ANY.RUN in your company for Effective Malware Analysis Are you from SOC and DFIR teams? – Join With 400,000 independent Researchers
Malware analysis can be fast and simple. Just let us show you the way to:
- Interact with malware safely
- Set up virtual machine in Linux and all Windows OS versions
- Work in a team
- Get detailed reports with maximum data If you want to test all these features now with completely free access to the sandbox: ..
Anti-Forensics and Attribution
The ArcaneDoor campaign demonstrated advanced anti-forensics capabilities, modifying core dump functions, disabling logging, and hooking authentication processes to hide their activities.
These operational security measures, combined with developing bespoke malware implants and chaining of zero-days, strongly suggest a state-sponsored threat actor.
While Cisco has released patches for the exploited vulnerabilities, organizations should urgently update their ASA firewalls and follow the recommended incident response procedures to detect and remediate potential compromises from this campaign.
Perimeter network devices like firewalls are lucrative targets for espionage actors because they provide a direct intrusion point into sensitive networks.
The ArcaneDoor campaign underscores the importance of prompt patching, secure configurations, and proactive monitoring of such critical infrastructure components.
Combat Email Threats with Free Phishing Simulations: Email Security Awareness Training ->Try Free DemoIndicators of Compromise
Likely Actor-Controlled Infrastructure:
192.36.57[.]181
185.167.60[.]85
185.227.111[.]17
176.31.18[.]153
172.105.90[.]154
185.244.210[.]120
45.86.163[.]224
172.105.94[.]93
213.156.138[.]77
89.44.198[.]189
45.77.52[.]253
103.114.200[.]230
212.193.2[.]48
51.15.145[.]37
89.44.198[.]196
131.196.252[.]148
213.156.138[.]78
121.227.168[.]69
213.156.138[.]68
194.4.49[.]6
185.244.210[.]65
216.238.75[.]155Multi-Tenant Infrastructure:
5.183.95[.]95
45.63.119[.]131
45.76.118[.]87
45.77.54[.]14
45.86.163[.]244
45.128.134[.]189
89.44.198[.]16
96.44.159[.]46
103.20.222[.]218
103.27.132[.]69
103.51.140[.]101
103.119.3[.]230
103.125.218[.]198
104.156.232[.]22
107.148.19[.]88
107.172.16[.]208
107.173.140[.]111
121.37.174[.]139
139.162.135[.]12
149.28.166[.]244
152.70.83[.]47
154.22.235[.]13
154.22.235[.]17
154.39.142[.]47
172.233.245[.]241
185.123.101[.]250
192.210.137[.]35
194.32.78[.]183
205.234.232[.]196
207.148.74[.]250
216.155.157[.]136
216.238.66[.]251
216.238.71[.]49
216.238.72[.]201
216.238.74[.]95
216.238.81[.]149
216.238.85[.]220
216.238.86[.]24The post Hackers Exploit Cisco Firewall Zero-Days to Hack Government Networks appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
But the giants they beat out are welcome to pitch self-developed drones for production contracts.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Aircraft are likely “already flying” material toward the beleaguered country, senior official says.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


