-
Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining activity. That’s according to the Microsoft Threat Intelligence team, which said the flaws have been weaponized since the start of April 2024. OpenMetadata is an open-source platform that operates as a
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new Google malvertising campaign is leveraging a cluster of domains mimicking a legitimate IP scanner software to deliver a previously unknown backdoor dubbed MadMxShell. “The threat actor registered multiple look-alike domains using a typosquatting technique and leveraged Google Ads to push these domains to the top of search engine results targeting specific search keywords, thereby
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Our State of Defense series continues with discussion with the CNO and the 4th Fleet.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Could Poland or Romania be eyeing the USAF’s old Warthogs?
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Program officials also say they’ll “reimagine” their upgrade plan, with new delays for some capabilities.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
If officials confirm it, Moscow would join the list of recent foreign infiltrators of U.S. water infrastructure.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In the wake of the recent disclosure of a critical vulnerability (CVE-2024-3400) affecting a leading firewall solution, Xiid Corporation reminds organizations that Xiid SealedTunnel customers remain secure. This latest vulnerability, currently unpatched and rated 10/10 on the CVSS (Common Vulnerability Scoring System), highlights the limitations of traditional security approaches.
Xiid SealedTunnel, the world’s first and only Zero Knowledge Networking (ZKN) solution, goes beyond Zero Trust architecture. Unlike today’s firewalls susceptible to zero-day exploits because of their break-and-inspect approach and the inevitable use of “smart” detection techniques that can and do fail, SealedTunnel is inherently resilient by design.
“This is a great example of why complex firewalls become their own security risk. Keep your firewalls simple, and just have them block all inbound access,” said Josh Herr, Head of Deployment and Integration at Xiid Corp. “Xiid SealedTunnel takes a fundamentally different approach. Our ZKN architecture ensures that data remains completely private and never exposed, even in the face of unknown threats.”
Xiid’s ZKN technology leverages the power of Zero Knowledge Proofs, allowing users to verify access rights without ever revealing sensitive information. This eliminates attack surfaces and renders data unreadable to unauthorized parties, even if a network breach occurs.
About Xiid Corporation
Xiid Corporation is a leading cybersecurity provider specializing in Zero Knowledge Networking solutions. Xiid’s flagship product, SealedTunnel, empowers organizations to achieve unparalleled security and privacy through a revolutionary approach that goes beyond traditional firewalls and zero-trust models. www.xiid.com
Contact
CEO
Steve Visconti
Xiid Corporation
steve@xiid.com
7753382174The post Xiid SealedTunnel: Unfazed by Yet Another Critical Firewall Vulnerability (CVE-2024-3400) appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A previously undocumented “flexible” backdoor called Kapeka has been “sporadically” observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm (aka APT44 or
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Security researchers at Cado Security Labs have uncovered a new variant of the Cerber ransomware targeting Linux systems.
This strain of the notorious malware has been observed exploiting a recent vulnerability in the Atlassian Confluence application to gain a foothold on targeted servers.
CVE-2023-22518: The Vulnerability Exploited
The primary attack vector for this Cerber variant is the exploitation of CVE-2023-22518, a vulnerability in the Atlassian Confluence application that allows an attacker to reset the application and create a new administrative account, as reported by Cado Security Labs.
This flaw, disclosed and patched earlier this year, has become a prime target for threat actors seeking to compromise Confluence servers.
Technical Details
The Cerber Linux ransomware is a highly obfuscated C++ payload, compiled as a 64-bit Executable and Linkable Format (ELF) binary and packed with the UPX packer.
This technique is employed to prevent traditional malware scanning and analysis.
Once the attacker gains access to the Confluence server through the CVE-2023-22518 exploit, they use the newly created administrative account to upload and install a malicious web shell plugin, Effluence.
Free Live Webinar for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register Here.This web shell provides a user interface for executing arbitrary commands on the compromised host.
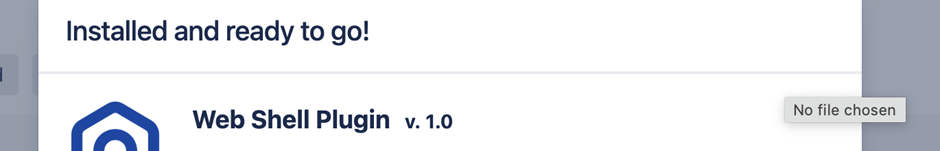
Recreation of installing a web shell on a Confluence instance The primary Cerber payload is then downloaded and executed through the web shell.
This payload is a stager responsible for setting up the environment and fetching additional components, including a log checker and the final encryptor payload.
The log checker payload, known as “agttydck,” is a simple C++ program that attempts to write a “success” message to a file.
This is likely a check for the appropriate permissions and sandbox detection.
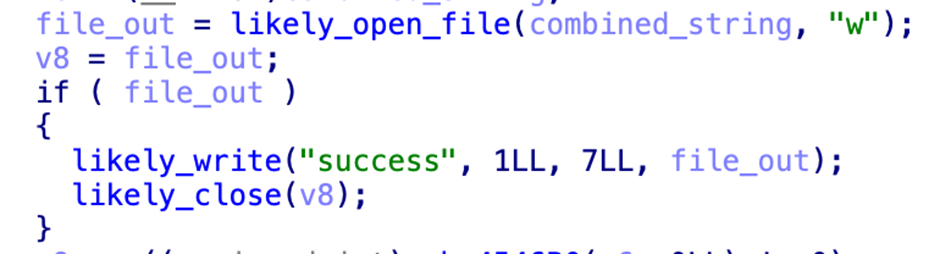
A cleaned-up routine that writes out the success phrase The final encryptor payload, “agttydcb,” is the core of the ransomware.
It systematically encrypts files across the file system, overwriting the original content with the encrypted data and appending the “.L0CK3D” extension.
A ransom note is also left in each directory, demanding payment for the decryption of the files.
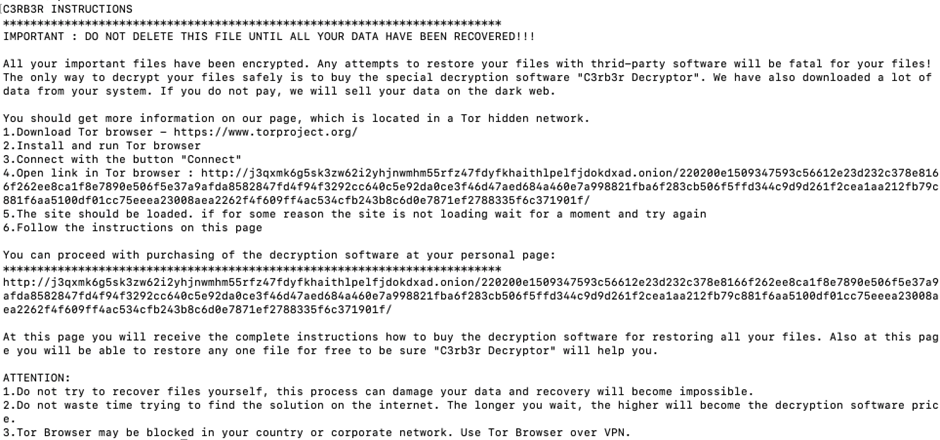
The ransom note left by Cerber The Cerber Linux ransomware exploited the Atlassian Confluence vulnerability, highlighting the importance of timely patching and vigilance in securing critical enterprise applications.
As threat actors continue to target vulnerabilities in popular software, organizations must remain proactive in their security measures to protect against such sophisticated attacks.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAPThe post Cerber Linux Ransomware Exploits Atlassian Servers to Take Full Control appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


