-
Security researchers have uncovered a “credible” takeover attempt targeting the OpenJS Foundation in a manner that evokes similarities to the recently uncovered incident aimed at the open-source XZ Utils project. “The OpenJS Foundation Cross Project Council received a suspicious series of emails with similar messages, bearing different names and overlapping GitHub-associated emails,” OpenJS
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Ahmed exploited a vulnerability in a decentralized cryptocurrency exchange’s smart contract by injecting fabricated pricing data, which triggered the generation of inflated fees totaling $9 million, which he subsequently withdrew in cryptocurrency.
Following the theft, Ahmed attempted to extort the exchange, proposing the return of a portion of the stolen funds ($7.5 million) on the condition that they refrain from involving law enforcement.
He exploited a vulnerability in Nirvana Finance’s smart contracts to buy cryptocurrency at a significantly discounted price and then resold it back to Nirvana at market value, draining $3.6 million—almost all their funds.
To hide the stolen funds, he employed various laundering techniques by converting the stolen crypto into different tokens (token-swap transactions) and then “bridged” these funds from the Solana blockchain to the Ethereum blockchain, essentially moving them across different networks.
At last, he converted everything to Monero, a privacy-focused cryptocurrency, and used anonymous exchanges and mixers to further obfuscate the trail.
Document Stop Advanced Phishing Attack With AI AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
Knowledge of Blockchain Security
Capitalizing on his in-depth knowledge of blockchain security, AHMED, a US citizen and senior security engineer at a prominent international technology company, carried out successful cyberattacks against two cryptocurrency exchanges.
His professional background in reverse engineering smart contracts, which involves analyzing and understanding their code to identify potential weaknesses, and blockchain auditing, a process focused on ensuring the security of blockchain transactions, provided him with the perfect toolkit for exploiting vulnerabilities within the exchanges’ smart contracts.
The vulnerabilities, which stemmed from flaws in the code governing the exchanges’ operations, allowed AHMED to manipulate data for his own gain and by executing these sophisticated attacks, he was able to steal over $12 million in cryptocurrency.
A New York resident, Ahmed (34), received a three-year prison sentence and three years of supervised release for exploiting vulnerabilities in cryptocurrency exchanges.
The court further mandated the forfeiture of $12.3 million and an undisclosed amount of cryptocurrency.
He is liable for over $5 million in restitution for the compromised exchanges and Homeland Security Investigations and the Internal Revenue Service’s Criminal Investigation Unit were commended for their contributions to the case.
According to the Justice Government, Shakeeb Ahmed, a former security engineer, was sentenced to 3 years in prison for hacking two decentralized cryptocurrency exchanges (DEXs) in a first-ever conviction for a smart contract hack.
He used his expertise in reverse engineering and blockchain audits to exploit vulnerabilities in the smart contracts and was also ordered to forfeit $12.3 million and a significant amount of cryptocurrency, along with $5 million in restitution to the affected DEXs.
The case highlights the collaborative effort between the Illicit Finance and Money Laundering Unit and the Complex Frauds and Cybercrime Unit to address cryptocurrency-related cybercrime.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post Ex-Security Engineer Jailed For Hacking Decentralized Cryptocurrency Exchanges appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The threat actor tracked as TA558 has been observed leveraging steganography as an obfuscation technique to deliver a wide range of malware such as Agent Tesla, FormBook, Remcos RAT, LokiBot, GuLoader, Snake Keylogger, and XWorm, among others. “The group made extensive use of steganography by sending VBSs, PowerShell code, as well as RTF documents with an embedded exploit, inside
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant risks to organizations. The vulnerability has been codenamed LeakyCLI by cloud security firm Orca. “Some commands on Azure CLI, AWS CLI, and Google Cloud CLI can expose sensitive information in
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Omni Hotels & Resorts has revealed that it was the target of a recent cyberattack, which resulted in the theft of customer information.
The hospitality giant has been working closely with a leading cybersecurity response group to investigate the incident and mitigate the impact on its guests.
Limited Customer Data Compromised
According to the company’s statement, the attack has impacted a subset of Omni’s customers.
The stolen data includes customer names, email addresses, mailing addresses, and information related to the company’s Select Guest Loyalty program.
The compromised data does not include sensitive financial information, such as payment details or social security numbers.
Omni Hotels & Resorts has reported the matter to law enforcement and is collaborating with cybersecurity experts to address the situation.
Document Stop Advanced Phishing Attack With AI AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
The company has taken swift action to shut down its systems and contain the data breach, with most of its systems now restored to full functionality.
Commitment to Guest Experience and Security
Despite the disruption caused by the cyberattack, Omni Hotels & Resorts has remained committed to maintaining its exceptional guest experience.
The company has continued to welcome guests and accept new reservations online and through its customer care center.
In a statement, Omni emphasized its dedication to the security of its systems and data, stating, “We take the security of our systems and data very seriously, and while this remains an ongoing investigation, Omni continues to collaborate with a leading cybersecurity response group and deploy all available resources to address the situation.”
The hospitality industry has been a frequent target of cyberattacks in recent years, underscoring the importance of robust cybersecurity measures and vigilance in protecting customer information.
Omni’s swift response and commitment to transparency in this incident serve as a reminder of the critical role that organizations play in safeguarding their customers’ trust.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAPThe post Omni Hotels & Resorts Hack: Attackers have Stolen Customer Information appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A new exploit campaign has emerged, targeting organizations that utilize Fortinet’s FortiClient EMS.
Dubbed “Connect:fun” by Forescout Research – Vedere Labs, this campaign leverages a critical vulnerability identified as CVE-2023-48788.
The campaign has been active since at least 2022 and has recently been observed exploiting the security management solution with increased vigor.
The Vulnerability: CVE-2023-48788
CVE-2023-48788 is an SQL injection vulnerability found within Fortinet’s FortiClient EMS. SQL injection is a type of attack that allows an adversary to interfere with an application’s database queries.
It can be used to view data that the attacker cannot normally retrieve, such as user information, or to manipulate database information.
Fortinet published an advisory about this vulnerability on March 12, 2024, and the proof of concept (PoC) for the exploit was made publicly available on March 21, 2024.
This disclosure seemingly acted as a catalyst for increased exploitation attempts by threat actors.
Document Stop Advanced Phishing Attack With AI AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
The Connect:fun campaign is particularly notable for its use of ScreenConnect and Powerfun as post-exploitation tools, marking it as Vedere Labs’ first-ever named campaign.
The incident that brought this campaign to light involved a media company whose FortiClient EMS was vulnerable and exposed to the internet.
The attack was not an isolated event. Scanning activity from the IP address 185[.]56[.]83[.]82 was observed targeting FortiClient EMS across various customer networks.
This activity began on March 21 and persisted through several days, indicating a concerted effort by the attackers to exploit the vulnerability across multiple potential victims.
The exploitation of CVE-2023-48788 poses a significant threat to organizations, as it can lead to unauthorized access and control over the FortiClient EMS.
This control can result in further malicious activities, including data theft, lateral movement within the network, and potentially a full-scale breach of the organization’s cyber defenses.
Mitigation and Defense Strategies
In response to the Connect:fun campaign, organizations are urged to take immediate action to protect their networks:
- Apply the Patch: Fortinet has released a patch to address CVE-2023-48788. Organizations should apply this patch without delay to close the vulnerability.
- Monitor Traffic: It is crucial to monitor the traffic reaching FortiClient EMS for signs of exploitation. An intrusion detection system (IDS) can be instrumental in identifying and responding to malicious activities.
- Web Application Firewall (WAF): Deploying a WAF can help block potentially malicious requests and provide an additional layer of security.
- Leverage IoCs and TTPs: Indicators of Compromise (IoCs) and Tactics, Techniques, and Procedures (TTPs) shared by cybersecurity researchers can be used to detect and prevent attacks.
Organizations using Fortinet’s FortiClient EMS must take proactive measures to secure their systems against this and other similar threats.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post Connect:fun Attacking Organizations Running Fortinet’s FortiClient EMS appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
TA558, a financially motivated threat actor identified in 2018, is targeting several countries but with utmost priority in Latin America.
Over 320 attacks have been observed from this particular threat actor, which involve using various tools and malware and compromising legitimate FTP servers and SMTP Servers.
Among the 320 attacks, 45 of them were targeted on Mexico, 38 over Colombia and 26 over Chile.
The sectors of interest seem to be the Industrial sector (22%), Service sector (16%), and Public sector (16%).
In addition, the threat actor has also been using Steganography techniques with images and text files.
TA558 Hackers Compromised 320+ Organizations
The threat actor used the compromised SMTP servers to send phishing emails to victims and also utilized the same SMTP servers for C2 infrastructure.

Phishing email (Source: Positive Technologies) Some of the SMTP servers used by this threat actor were found to have public directories that contained Malware logs of Stolen data.
Document Stop Advanced Phishing Attack With AI AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
The log files contained combined logs of credentials from well-known browsers, email accounts, and remote access credentials.
Moreover, these credentials belonged to regular users, public institutions, and various businesses.
In the initial phases of the investigation, researchers discovered an XLAM file in a phishing email from a compromised SMTP server.
When the attachment is opened with Excel, an EXE file named “packedtpodododod.exe” was downloaded from a C2 URL using the Excel macros.

File opened and a GET request is sent (Source: Positive Technologies) In addition, an RTF file was identified on the same C2 server alongside another EXE file, which is the exploit file for CVE-2017-11882.
When the final EXE file is downloaded and run, the final payload of the relevant malware, say AgentTesla, then uploads exfiltrated data to the C2 via FTP.

VB script file (Source: Positive Technologies) Further analysis revealed that the threat actor was using multiple malware families such as AgentTesla, Remcos, XWorm, LokiBot, Guloader, Formbook and SnakeKeylogger.
Attack Scenarios
Two attack scenarios were identified by the threat actor. One involves using an Excel document and steganography, and the other involves a Microsoft Word document.
Among these attack scenarios, the attack using an Excel document was the main scenario, which starts with a phishing email sent to the victim from the compromised SMTP server containing a malicious file “Cerere de cotatie.xla”.
When this file is opened, two requests are made to the C2 server for downloading a DOC and an RTF.
Once the RTF file is downloaded, another VBS file is downloaded from a paste[.]ee server.

File from past[.]ee server (Source: Positive Technologies) Following this, the VBS file proceeds to download and decode two image files that contain a base64 encoded malicious string that points to the next-stage payload.
The VBS file contains a PowerShell script to decode this base64 encoded string and proceeds to download the next-stage payload.

Image with encoded string (Source: Positive Technologies) Finally, the AgentTesla malware runs on the system which checks the execution environment.
Further, it also checks if the victim’s IP address is real. If these checks are successful, the malware proceeds to steal data from browsers, email clients, and remote access services and uploads it to the C2 server using FTP.
However, the second attack variant involving a Microsoft Word document has a similar methodology, but it does not use steganography techniques using images.
Instead, it directly downloads the AgentTesla malware using the RTF document.
Other variants of the attacks using Remcos, LokiBot, FormBook, Guloader, Snake Keylogger, and XWorm also use the first attack scenario for downloading and executing the malware on the victim system.
Nevertheless, the C2 and download servers differ for every malware and attack variant.
On further investigation, the FTP servers used by the threat actors belonged to legitimate websites that were also compromised for using them as C2 servers for data exfiltration.
There were also several legitimate companies with thousands of followers on social media.

Compromised website for C2 FTP (Source: Positive Technologies) Furthermore, the indicators of compromise can be viewed on the research blog published by Positive Technologies.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.The post TA558 Hackers Compromised 320+ Organizations’ FTP & SMTP Servers appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
The maintainers of the PuTTY Secure Shell (SSH) and Telnet client are alerting users of a critical vulnerability impacting versions from 0.68 through 0.80 that could be exploited to achieve full recovery of NIST P-521 (ecdsa-sha2-nistp521) private keys. The flaw has been assigned the CVE identifier CVE-2024-31497, with the discovery credited to researchers Fabian Bäumer and Marcus
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In today’s rapidly evolving digital landscape, organizations face an increasingly complex array of cybersecurity threats. The proliferation of cloud services and remote work arrangements has heightened the vulnerability of digital identities to exploitation, making it imperative for businesses to fortify their identity security measures. Our recent research report, The Identity Underground
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A group of cybercriminals known as “Blackjack” has launched a devastating attack on industrial control systems (ICS) worldwide.
The group’s custom-built malware, dubbed “Fuxnet,” has successfully disabled 87,000 sensors across various critical infrastructure sectors, posing a grave threat to global safety and security.
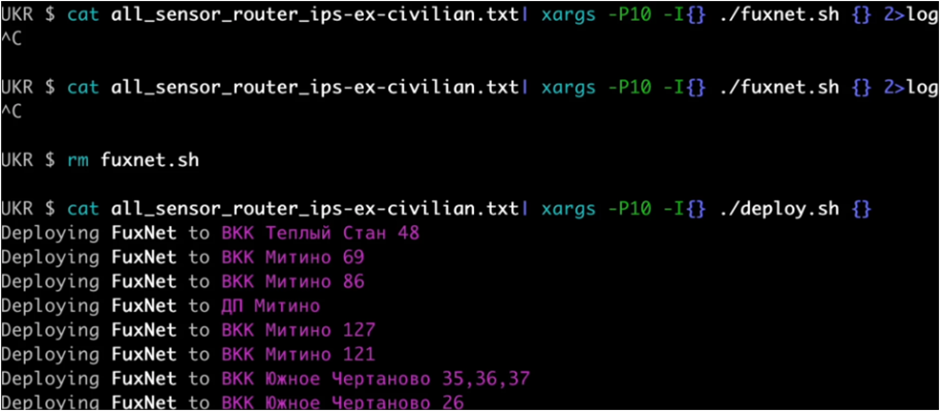
Fuxnet malware’s attack vector The Fuxnet malware, meticulously analyzed by the cybersecurity firm Claroty’s Team82, is a highly sophisticated and lethal piece of code.
It targets a wide range of ICS devices, including programmable logic controllers (PLCs), human-machine interfaces (HMIs), and other critical components forming the backbone of industrial operations.
Document Stop Advanced Phishing Attack With AI AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
Targeted Attacks on Vital Sectors
The Blackjack group has strategically targeted several vital industries, including manufacturing, energy, and water treatment facilities.
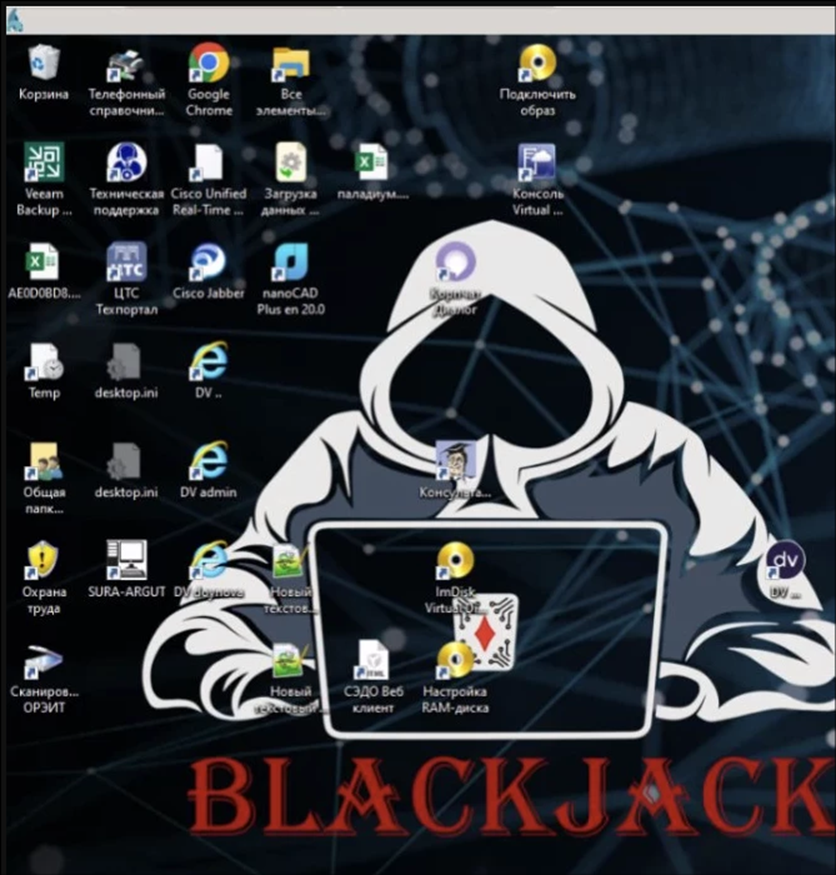
A defaced workstation showing a Blackjack image. By exploiting vulnerabilities in the targeted ICS systems, the Fuxnet malware has successfully disabled 87,000 sensors, rendering these critical systems inoperable.
“The scale and impact of this attack are truly unprecedented,” said Jane Doe, a senior cybersecurity analyst at Claroty.
“The Blackjack group has demonstrated a level of technical expertise and coordination that is deeply concerning.
Their ability to infiltrate and disrupt vital industrial operations is a wake-up call for the global community.”
Devastating Consequences and Ongoing Investigations
The consequences of the Fuxnet attack are far-reaching and potentially destructive.
Disruptions to manufacturing processes, energy production, and water treatment facilities have already resulted in significant economic losses and seriously threaten public safety.
Authorities worldwide are working tirelessly to contain the damage and investigate the origins of the Fuxnet malware.
Law enforcement agencies and cybersecurity experts are collaborating to identify the members of the Blackjack group and their motivations and develop effective countermeasures to prevent similar attacks in the future.
“This is a stark reminder of the critical importance of robust cybersecurity measures in the industrial sector,” said John Doe, a spokesperson for the International Cybersecurity Agency.
“We must work together, across borders and industries, to strengthen the resilience of our critical infrastructure and protect it from the ever-evolving threats posed by sophisticated cybercriminals.
“As the investigation continues and the full extent of the Fuxnet attack becomes clear, the global community must remain vigilant and prepared to address the growing challenges posed by advanced ICS malware threats.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAPThe post Blackjack Hackers Destroyed 87,000 Sensors Using Lethal ICS Malware appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


