-
Our State of Defense series continues with discussion with the CNO and the 4th Fleet.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Could Poland or Romania be eyeing the USAF’s old Warthogs?
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Program officials also say they’ll “reimagine” their upgrade plan, with new delays for some capabilities.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
If officials confirm it, Moscow would join the list of recent foreign infiltrators of U.S. water infrastructure.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
In the wake of the recent disclosure of a critical vulnerability (CVE-2024-3400) affecting a leading firewall solution, Xiid Corporation reminds organizations that Xiid SealedTunnel customers remain secure. This latest vulnerability, currently unpatched and rated 10/10 on the CVSS (Common Vulnerability Scoring System), highlights the limitations of traditional security approaches.
Xiid SealedTunnel, the world’s first and only Zero Knowledge Networking (ZKN) solution, goes beyond Zero Trust architecture. Unlike today’s firewalls susceptible to zero-day exploits because of their break-and-inspect approach and the inevitable use of “smart” detection techniques that can and do fail, SealedTunnel is inherently resilient by design.
“This is a great example of why complex firewalls become their own security risk. Keep your firewalls simple, and just have them block all inbound access,” said Josh Herr, Head of Deployment and Integration at Xiid Corp. “Xiid SealedTunnel takes a fundamentally different approach. Our ZKN architecture ensures that data remains completely private and never exposed, even in the face of unknown threats.”
Xiid’s ZKN technology leverages the power of Zero Knowledge Proofs, allowing users to verify access rights without ever revealing sensitive information. This eliminates attack surfaces and renders data unreadable to unauthorized parties, even if a network breach occurs.
About Xiid Corporation
Xiid Corporation is a leading cybersecurity provider specializing in Zero Knowledge Networking solutions. Xiid’s flagship product, SealedTunnel, empowers organizations to achieve unparalleled security and privacy through a revolutionary approach that goes beyond traditional firewalls and zero-trust models. www.xiid.com
Contact
CEO
Steve Visconti
Xiid Corporation
steve@xiid.com
7753382174The post Xiid SealedTunnel: Unfazed by Yet Another Critical Firewall Vulnerability (CVE-2024-3400) appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
A previously undocumented “flexible” backdoor called Kapeka has been “sporadically” observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The findings come from Finnish cybersecurity firm WithSecure, which attributed the malware to the Russia-linked advanced persistent threat (APT) group tracked as Sandworm (aka APT44 or
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Security researchers at Cado Security Labs have uncovered a new variant of the Cerber ransomware targeting Linux systems.
This strain of the notorious malware has been observed exploiting a recent vulnerability in the Atlassian Confluence application to gain a foothold on targeted servers.
CVE-2023-22518: The Vulnerability Exploited
The primary attack vector for this Cerber variant is the exploitation of CVE-2023-22518, a vulnerability in the Atlassian Confluence application that allows an attacker to reset the application and create a new administrative account, as reported by Cado Security Labs.
This flaw, disclosed and patched earlier this year, has become a prime target for threat actors seeking to compromise Confluence servers.
Technical Details
The Cerber Linux ransomware is a highly obfuscated C++ payload, compiled as a 64-bit Executable and Linkable Format (ELF) binary and packed with the UPX packer.
This technique is employed to prevent traditional malware scanning and analysis.
Once the attacker gains access to the Confluence server through the CVE-2023-22518 exploit, they use the newly created administrative account to upload and install a malicious web shell plugin, Effluence.
Free Live Webinar for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register Here.This web shell provides a user interface for executing arbitrary commands on the compromised host.
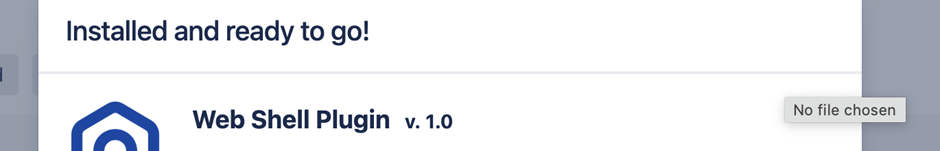
Recreation of installing a web shell on a Confluence instance The primary Cerber payload is then downloaded and executed through the web shell.
This payload is a stager responsible for setting up the environment and fetching additional components, including a log checker and the final encryptor payload.
The log checker payload, known as “agttydck,” is a simple C++ program that attempts to write a “success” message to a file.
This is likely a check for the appropriate permissions and sandbox detection.
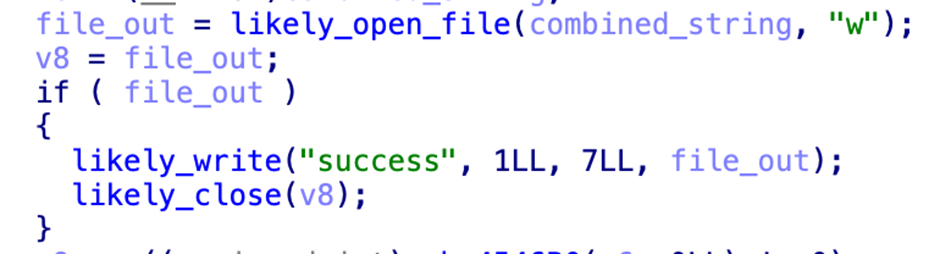
A cleaned-up routine that writes out the success phrase The final encryptor payload, “agttydcb,” is the core of the ransomware.
It systematically encrypts files across the file system, overwriting the original content with the encrypted data and appending the “.L0CK3D” extension.
A ransom note is also left in each directory, demanding payment for the decryption of the files.
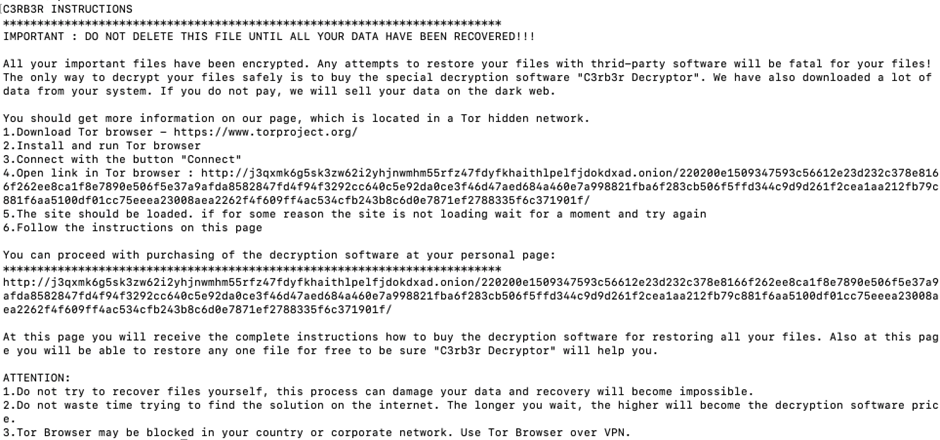
The ransom note left by Cerber The Cerber Linux ransomware exploited the Atlassian Confluence vulnerability, highlighting the importance of timely patching and vigilance in securing critical enterprise applications.
As threat actors continue to target vulnerabilities in popular software, organizations must remain proactive in their security measures to protect against such sophisticated attacks.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAPThe post Cerber Linux Ransomware Exploits Atlassian Servers to Take Full Control appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
Detecting source code vulnerabilities aims to protect software systems from attacks by identifying inherent vulnerabilities.
Prior studies often oversimplify the problem into binary classification tasks, which poses challenges for deep learning models to effectively learn diverse vulnerability characteristics.
To address this, the following cybersecurity analysts introduced FGVulDet, a fine-grained vulnerability detector that employs multiple classifiers to discern various vulnerability types:-
- Shangqing Liu from Nanyang Technological University
- Wei Ma from Nanyang Technological University
- Jian Wang from Nanyang Technological University
- Xiaofei Xie from Singapore Management University
- Ruitao Feng from Singapore Management University
- Yang Liu from Nanyang Technological University
FGVulDet Vulnerability Detector
Each classifier learns type-specific semantics, and researchers propose a novel data augmentation technique to enhance diversity in the training dataset.
Inspired by graph neural networks, FGVulDet utilizes an edge-aware GGNN to capture program semantics from a large-scale GitHub dataset encompassing five vulnerability types.

Five Vulnerability Types Previous works have simplified the identification of source code vulnerability into a binary classification problem where all defect-prone functions are labeled as 1.
This approach lacks accuracy because it does not consider types of particular vulnerabilities.
However, in contrast to this, the researchers’ approach focuses on fine-grained vulnerability identification and aims to learn prediction functions for distinct vulnerability types within a dataset.
Each function is categorized based on its vulnerability type to predict its vulnerability status.
Their framework has three core parts:-
- Data Collection
- Vulnerability-preserving Data Augmentation
- Edge-aware GGNN
On the other hand, researchers train multiple binary classifiers for different vulnerability types and aggregate their predictions through voting during the prediction phase.
This task is difficult as obtaining high-quality datasets covering a broad range of vulnerabilities requires specialist knowledge.
.webp)
The framework of FGVulDet (Source – Arxiv) GGNN is a very famous source code modeling approach that is limited to node representations without considering the edge information.
In this case, it’s aimed at proposing an edge-sensitive GGNN that can effectively use edge semantics in vulnerability detection.
Each type of vulnerability has its own binary classifier, which is trained by using datasets of both vulnerable and non-vulnerable functions.
The final prediction is made through majority voting across all the classifiers.
Since the researchers’ dataset includes common vulnerabilities so, it can be extended for detecting others as well.
On the other hand, FGVulDet employs multiple classifiers and a novel data augmentation technique for effective fine-grained vulnerability detection.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.The post FGVulDet – New Vulnerability Detector to Analyze Source Code appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
-
DMARC is targeted by hackers as this serves to act as a preventative measure against email spoofing and phishing attempts.
They compromise DMARC (Domain-based Message Authentication Reporting and Conformance) so that they can evade email authentication protocols, consequently enabling them to mimic authentic senders and mislead recipients.
This way they can put up more conceivable and advantageous phishing campaigns that lead to either making money or stealing data.
Cybersecurity researchers at ProofPoint recently discovered that North Korean hackers are actively abusing the DMARC to legitimize their illicit emails.
DMARC Abuse
Proofpoint tracks the North Korean state-aligned group TA427 (aka Emerald Sleet, APT43, THALLIUM, Kimsuky), which conducts phishing campaigns targeting experts on U.S. and South Korean foreign policy for the Reconnaissance General Bureau.
Since 2023, TA427 has directly solicited opinions from foreign policy experts on nuclear disarmament, U.S.-ROK policies, and sanctions via innocent conversation-starting emails.
Free Live Webinar.for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register HereResearchers observed a steady and sometimes increasing stream of this activity.
While TA427 consistently relies on social engineering and rotating email infrastructure, in December 2023, it began abusing lax DMARC policies for persona spoofing and incorporated web beacons for target profiling in February 2024.
.webp)
Volume of TA427 phishing campaigns (Source – ProofPoint) TA427 is a skilled social engineering threat actor likely supporting North Korean strategic intelligence collection on U.S. and South Korean foreign policy initiatives.
By engaging targets over extended periods through rotating aliases and innocent conversations, TA427 builds rapport to solicit opinions and analysis, especially around foreign policy negotiation tactics.
Leveraging customized, timely lure content and spoofing familiar DPRK researchers, TA427 requests targets share thoughts via email, papers, or articles rather than directly delivering malware or credential harvesting.
This direct input approach may fulfill TA427’s intelligence requirements while the correspondence insights improve future targeting and connection building for additional engagement.
The goal appears to be augmenting North Korean intelligence to inform negotiation strategies.
.webp)
Timeline of real-world events based on international press reporting (Source – ProofPoint) Their lures include invitations to events on North Korean affairs, inviting perspectives on deterrence policies, nuclear programs, and possible conflicts.
It involves moving conversations between email addresses, such as those of individuals being targeted and their workplaces.
TA427 masks itself in a number of ways as think tanks, non-governmental organizations (NGOs), media outlets, educational institutions, and governmental bodies utilize DMARC abuse, typosquatting, and free email spoofing for legitimization
.webp)
Timeline of real-world events based on international press reporting (Source – ProofPoint) A different tactic from early February 2024 performs reconnaissance over the victim’s active email as well as the recipient environment through web beacons.
One of the most frequently seen actors tracked by Proofpoint is TA427 which constantly adapts its modus operandi, infrastructure elements or even avatars to tactically target experts to steal information or gain initial access for intelligence purposes rather than profit maximization.
IoCs
.webp)
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.The post North Korean Hackers Abuse DMARC To Legitimize Their Emails appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
¶¶¶¶¶
CYBERSECURITY / DEFENSE / INTELLIGENCE


